Cybersecurity Resources
Learn to protect your most critical systems and data with these free, in-depth PAM and IT Security resources. Search our library of webinars, videos, whitepapers, case studies, and more to get started with Privileged Access Management, get the most from Delinea’s solutions, and hear inspiring stories of PAM success from companies just like yours.
Looking for something specific? Search here:
Video

Privileged Access Management is Evolving to Extended PAM
Video
The Case for Extended Privileged Access Management
Video
What is Extended Privileged Access Management?
Whitepaper

Australian Essential Eight Compliance
Free Tool

Unix Privileged Account Discovery Tool
Whitepaper

Evolving from PAM to Extended PAM
Free Tool
Active Directory Weak Password Finder
Whitepaper

Cyber Insurance Research - If you get it, be ready to use it
Infographic
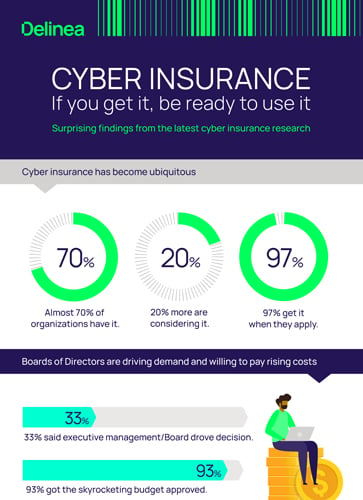
Cyber Insurance: Findings from the latest research
Case Study

Barrett Steel
Case Study

Robert Weed
Whitepaper

