Enforce least standing privilege across public clouds
Privilege Control for Cloud Entitlements
Continuously reduce cloud infrastructure risk by centralizing authorization
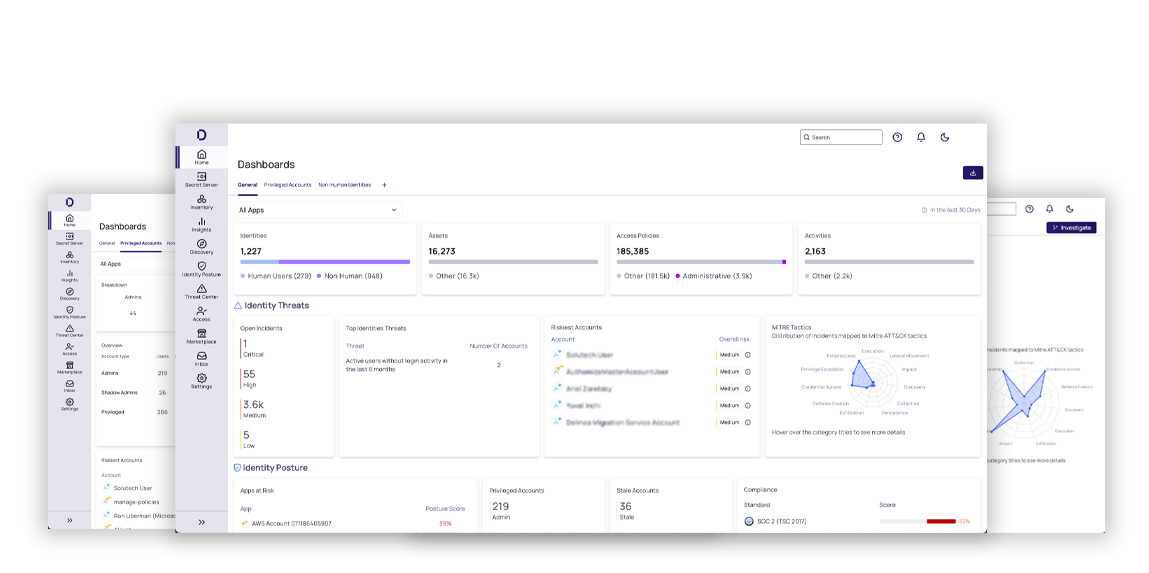
Reduce the risk of overprivileged & misconfigured identities
Enforce Least Privilege
Right-size entitlements to limit risk but enable productivity.
Identify riskiest identities
Find misconfigurations and normalize privileged behavior across the cloud.
Continuous discovery
Find identities and their entitlements in constantly changing complex cloud environments.
Proactively gain control of your multi-cloud infrastructure
Continuously discover and visualize all identities, accounts, and their access across Google, Amazon, and Microsoft clouds to identify anomalous behavior and refactor privileges.
Delinea provides security leaders with deep context into cloud and identity usage to discover excess privilege and limit authorization across multi-cloud infrastructure to reduce risk.

Continuous discovery
Find over-privileged users, shadow admins and stale accounts
Gain
visibility
View all identities and their access pathways across public multi-cloud infrastructure.
Fix misconfigurations
Understand misconfigurations and normalize privileged behavior across the cloud.
Enforce least privilege
Right-size entitlements to limit risk but enable productivity.
Unify administration
Deliver fast time-to-value and lower total cost of ownership with comprehensive governance of privileges in the cloud-native Delinea Platform.
Privilege Control for Cloud Entitlements Supports extended PAM
The standard definition of PAM isn’t sufficient for the growing risk of cyberattacks. We believe PAM must address the exploding number of identities and today’s IT complexities.
Our products provide effective authorization controls for an identity-centric approach to security.

Start a Free 30-Day Trial

5 Steps to Achieving Identity Security in the Cloud
Attend this webinar to learn about identity security in the cloud with a 5-step approach to gain visibility, find and fix misconfigurations, and protect sensitive users and data.

