Cybersecurity Resources
Learn to protect your most critical systems and data with these free, in-depth PAM and IT Security resources. Search our library of webinars, videos, whitepapers, case studies, and more to get started with Privileged Access Management, get the most from Delinea’s solutions, and hear inspiring stories of PAM success from companies just like yours.
Looking for something specific? Search here:
Video

Delinea Privileged Access Management Explained
Whitepaper

The Path to Zero Trust Starts with Identity
Free Tool

Server Suite Free
Whitepaper

NIST Security Measures for E.O. 14028
Solution Brief

Secret Server + Privilege Manager
Free Tool
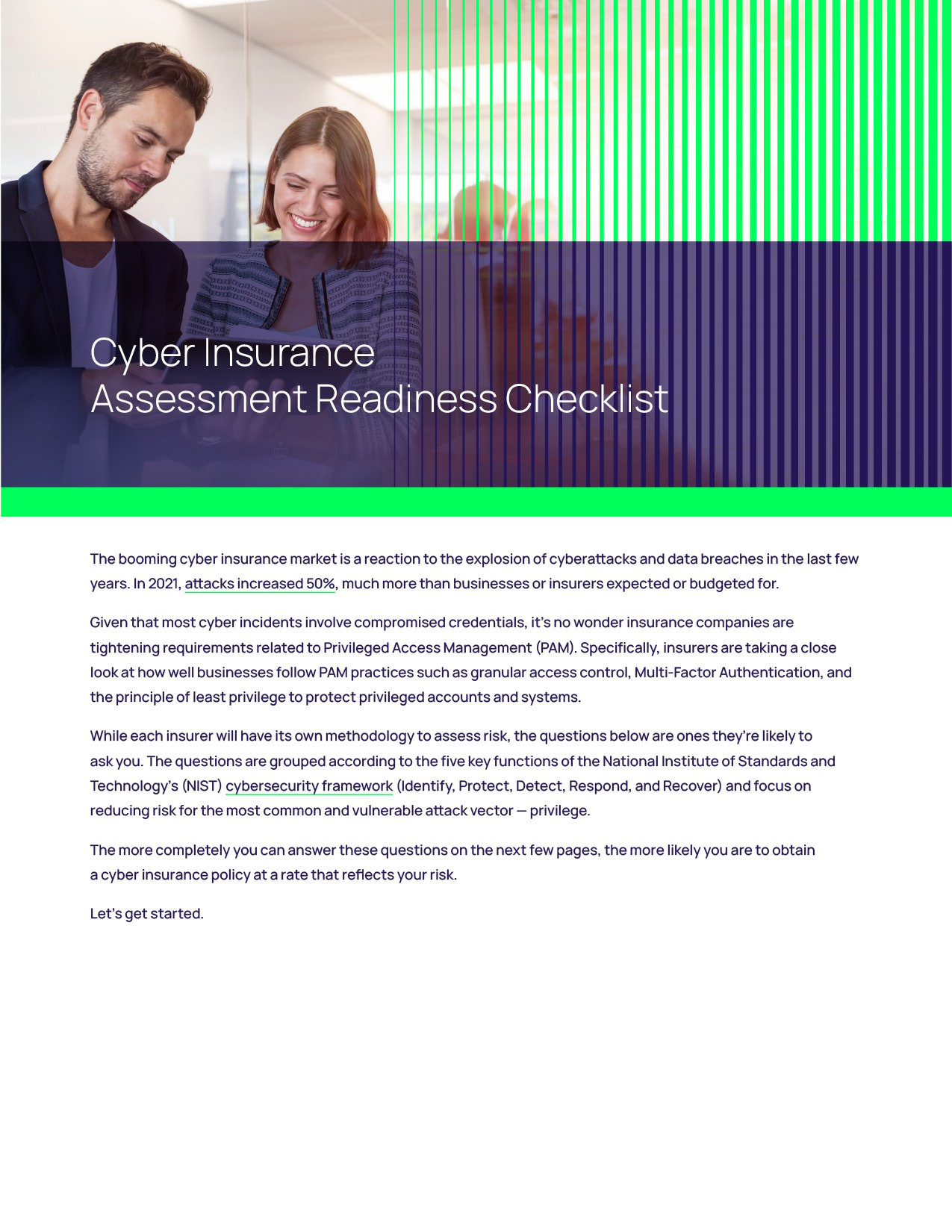
Cyber Insurance Readiness Checklist
eBook

Conversational Server Access Security
Whitepaper

How to Instantly See Privileged Account Abuse
Whitepaper

PAM Maturity Model
Whitepaper

Beyond Password Managers
Free Tool

Privileged Access Management Checklist
Whitepaper

