Cybersecurity Resources
Learn to protect your most critical systems and data with these free, in-depth PAM and IT Security resources. Search our library of webinars, videos, whitepapers, case studies, and more to get started with Privileged Access Management, get the most from Delinea’s solutions, and hear inspiring stories of PAM success from companies just like yours.
Looking for something specific? Search here:
Whitepaper

Cloud Automation is the Key to Future-proofing Cybersecurity
Infographic
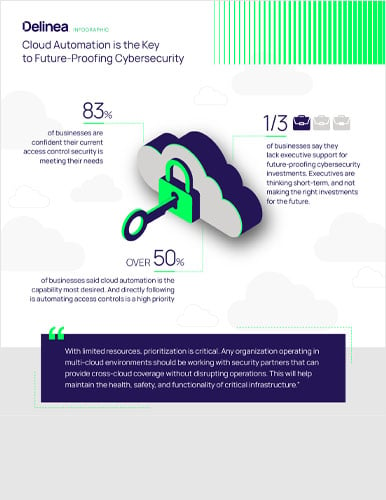
Cloud Automation is the Key to Future-proofing Cybersecurity
Case Study

Large Hospital System Case Study
Infographic
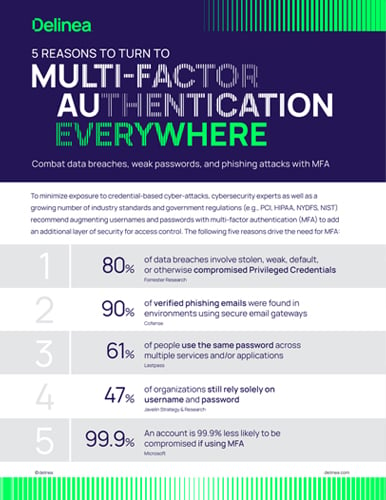
Turn to MFA Everywhere
Solution Brief

Adaptive Multi-Factor Authentication for Privileged Access
Solution Brief

How to Apply Zero Standing Privileges
Solution Brief

Secret Server for Business Users
Whitepaper

Best Practices for Verifying Privileged Users with MFA Everywhere
Whitepaper

IoT Security Challenges: The Risks and How to Minimize Them
Infographic
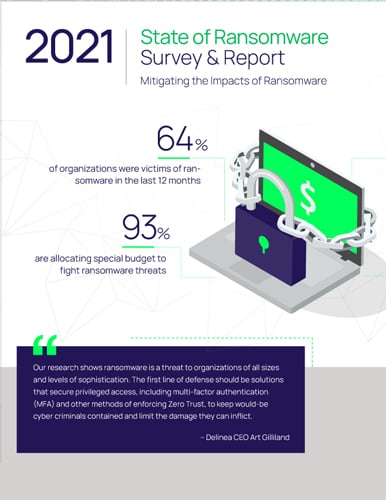
Ransomware Survey Report
Datasheet

Delinea Corporate Brochure
Free Tool

