Reduce cloud development pipeline risk with CIEM in these 3 steps

Authomize
Protect your organization’s software development pipeline or risk catastrophic consequences. By accessing the software development pipeline, malicious actors could steal valuable IP, slow production, or even insert malware that could be shipped with the product.
Organizations must prioritize securing their software development pipelines as these pipelines provide cybercriminals a channel for causing major damage.
Unfortunately, assets such as cloud applications and services used in the development process are exceedingly difficult to secure due to the complex nature of identity and access controls involved.
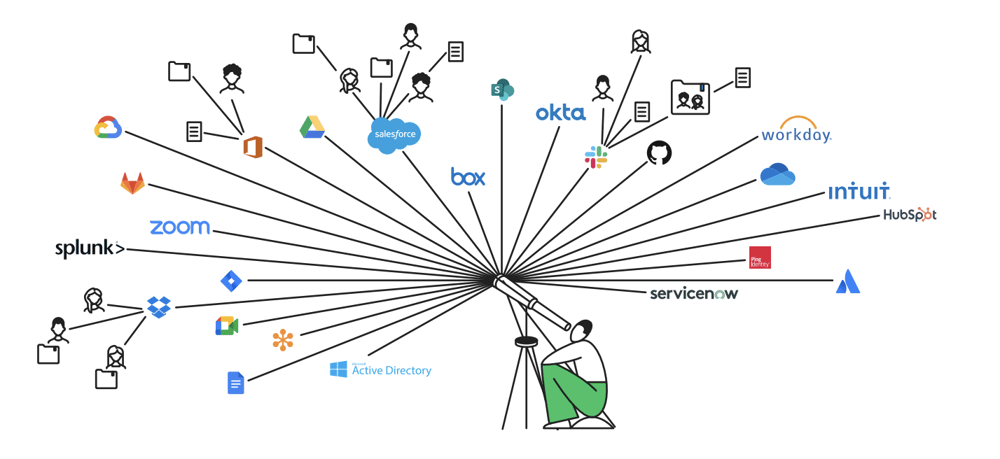
Cloud Infrastructure Entitlement Management (CIEM) provides visibility and control over identity and access use across all cloud applications and services, so you can reduce risk and safeguard your development pipeline.
Read on to see how CIEM addresses cloud development security challenges.
Challenges to securing identities and access to cloud infrastructure and applications

Identity is the key to access in the modern cloud-based development pipeline and a prime target for attackers to exploit.
According to research by the Identity Defined Security Alliance (IDSA) released in June 2022, 84% of organizations experienced an identity-related breach in the previous year. These breaches stem from many factors:
1. Exploding identities
A whopping 98% of security leaders who took part in the IDSA survey reported that the number of human and machine identities is increasing rapidly, primarily driven by cloud adoption, third-party relationships, and automation.
2. Lack of visibility
As the number of identities scales across a broad range of applications and services, traditional Identity and Access Management (IAM) structures can’t provide the full breadth of visibility required to secure them. This is especially true of systems built primarily for on-premise Identity and Access Management.
For example, security teams using traditional IAM solutions struggle to track federated identities as they assume roles in AWS and when developers bring their own identities into the organization’s private GitHub repository.
Organizations can’t tell if or how human and machine identities are using their access privileges in the cloud, so they don’t know if it’s necessary to retain them.
3. Overprivileged identities
Most organizations habitually provide users with more privileges than necessary to do their work or leave privileges in place long after a job is done. Recent research highlights worrisome violations of the principle of least privilege, which calls for limiting privileges to the absolute minimum.
According to Gartner’s Innovation Insight for Cloud Infrastructure Entitlement Management, “The vast majority of granted entitlements in IaaS are unnecessary. More than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted, which greatly increases the attack surface for account compromises.”
As more organizations adopt cloud development practices, the current situation isn’t sustainable. It’s time for a new generation of solutions to extend the capabilities of PAM and IAM to the cloud.
Three steps to overcoming the challenges of cloud identity management
Delinea's Privileged Access Management (PAM) enables organizations to securely manage privileged credentials and provide just-in-time, just-enough access. Authomize CIEM adds an additional layer of security, extending visibility to cloud infrastructure and applications and providing powerful, actionable privilege analytics.
With the combination of these solutions, you can reduce your identity and access threat surface, harden your security posture, and detect threats from malicious actors.
Step 1: Increase visibility over your attack surface
Track the entire path each identity takes through all groups, roles, and environments, such as jumping from an IaaS to a SaaS environment like AWS to GitHub.
Using native connectors and a universal REST API, Authomize collects access data from all cloud environments, including IaaS, SaaS, IAM, and home-grown applications, and surfaces that data for you.
Step 2: Set baselines for access privileges
When you see the full path, you’ll understand which privileges are used regularly and which have gone stale. With that information, you can review access levels, determine the level of access each identity really needs, and adjust accordingly.
Authomize helps you give reviewers context to decide whether to keep or revoke a privilege. Context, for example, access privilege not being used for 60 days, takes the guesswork out of reviews and provides justifications for decisions.
Step 3: Set policies and continuously monitor for risky changes
As your organization goes through the joiner-mover-leaver lifecycle, maintain your secure baseline by setting policies, tracking usage, and detecting when a privilege hasn’t been used.
Policies can also cover issues not directly tied to usage. Additional policy types can detect when an admin doesn’t have Multi-Factor Authentication (MFA) enabled on their account or if a repository doesn’t have the recommended protections. They can also be used to detect potential escalation paths.
One clear example of such a risk would be the creation of a new admin. If an attacker were able to exploit an escalation path, such as creating a new EC2 in AWS and become an admin, the attacker would become an admin everywhere. Changing their privileges inside of the IdP would also allow the attacker to pose a serious risk to the organization.
Policies that are continuously monitored alert you when risks are identified so you can act. For example, unused accounts can have their privileges revoked in accordance with least privilege best practices.
Authomize’s Identity Threat Detection and Response (ITDR) protects your IAM infrastructure from attackers by detecting such changes and alerting the security team so that they can take appropriate action.
Security in layers
Security is never a magic bullet.
Combining Authomize with Delinea PAM adds a layer of security that hardens your cloud security posture and strengthens your ability to respond effectively to a cyberattack. Authomize complements Delinea’s in-depth visibility of privileged access by extending visibility over all identities, assets, access privileges, and activities across your cloud environments.
Learn more about the importance of least privilege and how Authomize’s platform enables organizations like yours: The Path Towards Your Least Privilege Environment.

Start your least privilege journey here



