Get complete application control management with CylancePROTECT and Privilege Manager

Steve Goldberg
Delinea customers are constantly requesting integrations with other products in their arsenal, especially other security products. Delinea’s product team for Privilege Manager—our least privilege and application control product—is asked to work with CylancePROTECT® day after day. Our common customers are using both Delinea and Cylance products on the endpoint to provide multiple layers of malware protection. The basis of the request for integration was to use Cylance’s real-time AI-driven analysis to automatically build Delinea’s allowlist, denylist, and privilege elevation policies.
Below, I’ll outline 2 key points of integration:
On-demand reputation checks
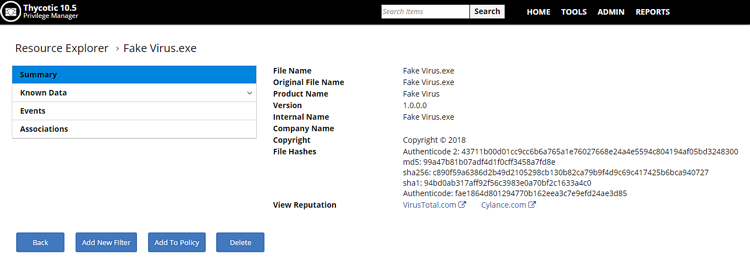
The first, and most obvious, point of integration is the ability to view the threat details of all files that Delinea has discovered on the endpoint. From the Delinea Privilege Manager interface, a user can check the Cylance score and threat details of the application or file in question.
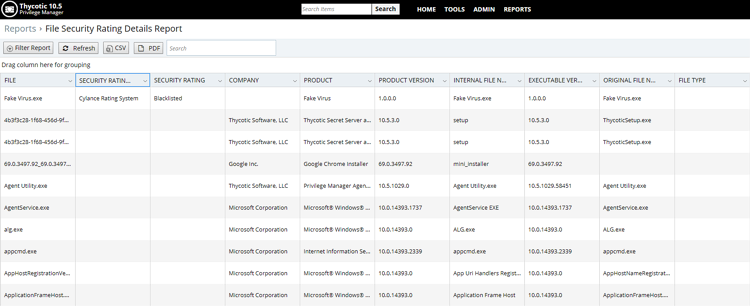
Additionally, the screenshot below shows a report of all inventoried applications along with Cylance’s security rating which can be used to build policies for known safe and malicious applications. Simply put, we’ve bridged the interfaces so it’s easy to navigate between the two and to view Cylance data from within Privilege Manager. We found that, typically, different teams were managing each product, so this integration makes it easy to communicate across teams and ensure both get value from the products.
Automatic workflows and remediation based on risk score
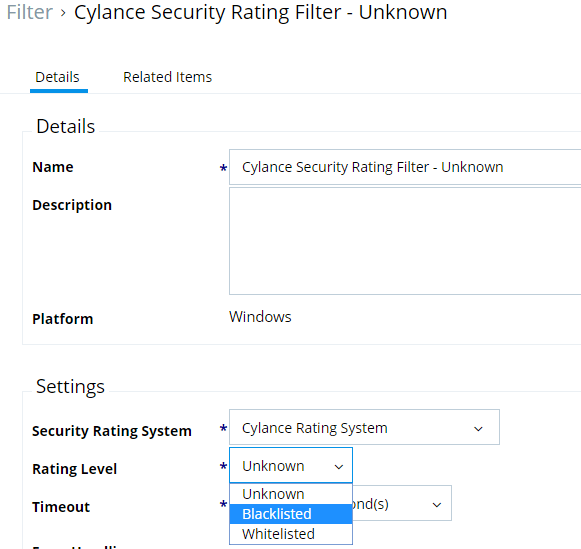
Delinea Privilege Manager can build rules that target specific applications and take a corresponding remediating action. Our customers will usually begin in “learning mode” which allows users to understand what applications are being used without taking any action. But what about currently unknown applications or potentially malicious software that your end users download in the future? Privilege Manager will implement what are called “catch-all” policies that will only be triggered if the preceding policies do not target this unknown application. As you can see in the screenshot below, a policy can be created for what Cylance deems a good, bad, or unknown application. The customer can then decide what remediating action is then taken on these kinds of apps.
Depending on how much you want to lock down your endpoints, typical catch-all remediating actions are: block execution, allow only during specified times of day, require an end user justification, or force an automated approval workflow to allow execution to continue once approved or denied by an administrator.
This functionality is intended to increase security on the endpoint, ease the burden of configuring Privilege Manager policies, and reduce frustration for our customer’s end users. Based on the results of the real-time reputation returned from Cylance, Privilege Manager will ensure end users can safely run the applications they need to do their job. With the power of both products working together, security teams can ensure they’ve decreased the attack surface on endpoints while maintaining end-user productivity.
Now it’s up to our customers to implement this integration. How far you take it will depend on your need for increased protection and your company culture around locking down an end user’s machine. Reach out and tell us how you’ve put this new feature into action!
Implementing Least Privilege shouldn't be hard