A guide to managing and securing privileged users

Barbara Hoffman
Organizations often have two to three times more privileged user accounts than individual employees. Securing these special accounts is vital to protecting sensitive information and critical systems from cyberattacks.
Privileged users require special handling, training, and oversight. To help people stay productive, you must provide appropriate access for privileged users while also minimizing risk to the organization.
Read on to learn:
- How privileged users differ from standard users.
- Risks associated with the compromise and misuse of privileged user accounts.
- How privileged user management (PUM) makes your organization less vulnerable.
You’ll gain a practical understanding of different types of users with a focus on privileged users and privileged user management, including what privileged users are, where they’re located throughout your organization, and how they function. Most importantly, you’ll understand the risks associated with privileged users and how to best protect IT systems and sensitive data.
Key Privileged User Definitions
To set the stage, let’s define important terms you need to know about privileged users, privileged accounts, and privileged user management.
What is a privileged user?
A privileged user is a person authorized to access critical IT systems and conduct activities that standard users have not been granted permission to perform. Privileged users are often Domain Administrators, Server Administrators, or other IT experts who configure hardware/software, make changes to systems, troubleshoot, and conduct IT activities on behalf of the organization.
That said, privileged users can also be business users or developers who can access and manipulate sensitive data, such as PII, corporate IP, or financial information.
People who have access to SaaS applications (like HR or finance systems) are also privileged users. So are people who retain local administrative rights to workstations as they can make configuration changes, add and remove applications, and execute programs.
The elevated level of permissions associated with privileged users makes their credentials attractive assets for cybercriminals to target via social engineering and phishing strategies.
What’s the difference between a privileged user and a privileged account?
Privileged users have unique identities, typically tied to Active Directory, Azure or other identity management systems. A privileged account, on the other hand, can be shared by multiple people. For example, everyone in a Group could have permission to access a privileged account for a particular function.
Although IT staff can be considered privileged users, they typically have multiple accounts that they use in different situations. In most organizations, IT staff have one user account with standard-level permissions for everyday work and a separate privileged account for performing operations that require elevated permissions.
For example, a privileged account might be used by an IT professional to access servers and perform an upgrade, modify settings, or conduct general maintenance. They may, in fact, leverage multiple privileged accounts, which allow them to access different systems and perform different functions.
 Examples of privileged accounts that have elevated permissions are:
Examples of privileged accounts that have elevated permissions are:
- Domain Admin accounts – authorized to make changes to global policies that impact all the servers, workstations, and users connected to that domain.
- Server Admin accounts – take care of Windows and Unix/Linux servers.
- Root or Superuser accounts – a special user account in Unix-like operating systems that has broad, powerful read and write privileges.
- System Admin accounts – take care of networks, computers, and other enterprise systems.
- Local Admin accounts – have permission to do anything but restricted to one machine.
Another key difference: A privileged user is a human being, whereas a privileged account can be leveraged by non-human, machine identities and services.
Examples of non-human privileged accounts that have elevated permissions are:
- Accounts that run and manage Windows applications, services, and scheduled tasks.
- IIS application pools (.NET applications).
- Networking equipment accounts that give access to firewalls, routers, and switches.
- Systems within a DevOps toolchain.
In practice, non-human accounts like these can be more difficult to discover and secure because they don’t have a unique privileged user responsible for them. Without oversight, you may not know if human accounts are compromised, and they’ll fall outside the range of your incident response activities.
If you focus only on the privileged user aspect of privilege management, you will miss the riskiest types of accounts.
The more privileged users and privileged accounts, the higher your risk
Virtually all organizations have unknown, unmanaged privileged user accounts. Some may have thousands.
This can happen for various reasons:
- A privileged user’s access was never disabled after they left the organization.
- An account is utilized less and less often until it becomes obsolete and is abandoned.
- Default accounts for new devices and workstations were never disabled.
Every unknown or unmanaged privileged user account presents a risk:
- An employee may access it to perform unauthorized tasks, intentionally or unintentionally, violating compliance mandates and increasing your liability.
- A disgruntled ex-employee who retains privileged access can knowingly gain unauthorized access to restricted data.
- A cybercriminal can find the account and penetrate your organization, steal information, and wreak untold havoc.
Without proactive management, it only takes one compromised privileged user account to become a catastrophe.
How attackers leverage privileged users
It’s much easier to steal a trusted insider’s credentials than it is to break through the firewall.
Most attackers take a methodical, multi-step approach to gain access to your most critical systems and data. They often perform patient and stealthy reconnaissance, with the goal of stealing credentials and impersonating privileged users or finding ways to circumvent the need to use credentials at all. They frequently start by taking over privileged user accounts that are using default or common passwords.
These tactics give them a foot in the door so they can elevate their access at will and exploit applications, data, and key administrative functions.
If these privileges are left unmanaged and unmonitored you may not even know if they are compromised
How far they get depends on the level of permissions the compromised privileged user account has. Unfortunately, many privileged users have standing access that is typically unnecessary to perform their jobs. If these privileges are left unmanaged and unmonitored you may not even know if they are compromised.
What’s worse, even in the most sophisticated organizations, privileged user accounts often use the same credentials to access multiple IT systems. So if an attacker compromises one account, they can move laterally throughout your IT environment, unless they are contained with additional security controls.
Challenges of Privileged User Management
Organizations want to follow security best practices, yet the complexity of managing privileged users creates a challenge for even the most well-intentioned IT staff.
Too many organizations rely on spreadsheets to keep track of privileged user accounts and credentials and attempt to govern them manually. These practices are inefficient, increase your risk, and are impossible to scale as your organization adds more privileged users.
You could add more processes and policies to restrict the permissions of privileged users, but there are limits to that approach as well. IT organizations are on the hook to provide people with appropriate access without friction. No one—standard user nor privileged user—wants to juggle multiple passwords, multiple authentication challenges, or multiple approval steps to gain the access they need to do their job.
So, what can you do to make privileged users productive and secure?
Privileged User Management and PAM
Privileged Access Management (PAM) relies on policies to control who can access sensitive systems and information, and what types of privileged activities they can conduct, under what conditions.
With PAM, all privileged accounts throughout your enterprises—both human-privileged users and non-human machine identities and service accounts—rely on credentials to control access and behavior. PAM solutions limit authorized access by creating, storing, and managing privileged credentials (passwords, keys, and secrets) in a secure vault. Additionally, PAM manages the full lifecycle of all types of privileged accounts, from discovery and provisioning to rotation and decommissioning.
With PAM, you can track privileged account activity and the behavior of each privileged user individually. You can add layers of approvals, session monitoring, and recording for continuous oversight. Enterprise-level analytics included in comprehensive PAM allows you to demonstrate compliance to auditors and executives. Your IT and security team can work together seamlessly to protect privileged users, prevent unauthorized privileged behavior, and contain cyber incidents.
How to secure different types of privileged user accounts
Domain Admin Accounts
What is it? The Domain Admin account has full access to almost all resources in the domain, including the Active Directory (AD) controller.
What’s the risk? Since this is a default on domain controllers, workstations, and member servers, if compromised or misused, it has broad access across the network.
What to do: Only a limited number of users should be given access to this type of account, and all activity should be actively monitored and routinely audited. Establish a formal approval process to assign just-in-time, just-enough access to these accounts, rather than standing, broad access.
Server Admin Accounts
What is it? These accounts are used to run Windows and Unix servers.
What’s the risk? If a cybercriminal gains access to a server, they could slow down or halt business operations, exfiltrate data, or cause other damage.
What to do: Rather than giving a group of Server Admins persistent permissions to access any server, any time they want, they must be limited by conditional policies. They must be granted the specific credential to access a server and their identity must be authenticated. Only then can their privileges be elevated, and then only for a short time.
Privileged Data User Accounts
What is it? This is a standard user account that has access to sensitive or privileged data: a broker with access to financial records, an accountant with access to tax documents, a doctor with access to patient data, a lawyer with access to sensitive client information.
What’s the risk? Since these are often run-of-the-mill user accounts that just happen to have extraordinary access, they may not be monitored or audited, and the password policy may not reflect their sensitive nature.
What to do: Perform a Data Risk Assessment to identify privileged accounts and the users who have access to them, then take steps to not only harden the application housing the data but also limit access by regular accounts. Ensure those accounts are subject to higher security scrutiny and protocols.
Emergency / Break Glass Accounts
What is it? In a critical incident, certain users may need access to privileged systems or accounts. An emergency account, which is disabled by default, can serve as an alternate way of accessing important systems. These types of accounts are reserved for emergencies, such as a cyberattack, which limits access to usual admin accounts.
What’s the risk? Since these accounts have access to sensitive systems when they are enabled, if they’re commandeered by an attacker, they could be used as a back door.
What to do: Limit access to these accounts, monitor actively, and ensure they’re only available in case of emergency, and not as a back door to sensitive data or systems.
Local Administrator Accounts on Workstations
What is it? Every workstation has an administrator account. The default local administrator account is the first account created. This account allows a workstation user to install printers, change languages, and install applications, etc.
What’s the risk? This is one of the main culprits of employees being overprivileged since it is often given to employees by default and grants them excess access, which they don’t necessarily need. If an employee falls victim to a phishing attack that installs malware on their workstation, a cybercriminal could gain access to the local account, giving them a foothold.
What to do: Remove default access to this account or disable it to prevent unauthorized use. Allow workstation users to conduct low-risk activities such as installing approved applications through the use of allow and deny lists.
Strategies for empowering privileged users
Privileged users want to do the right things and follow best practices. As a security leader, your role is to empower your privileged users so they can act securely without getting frustrated.
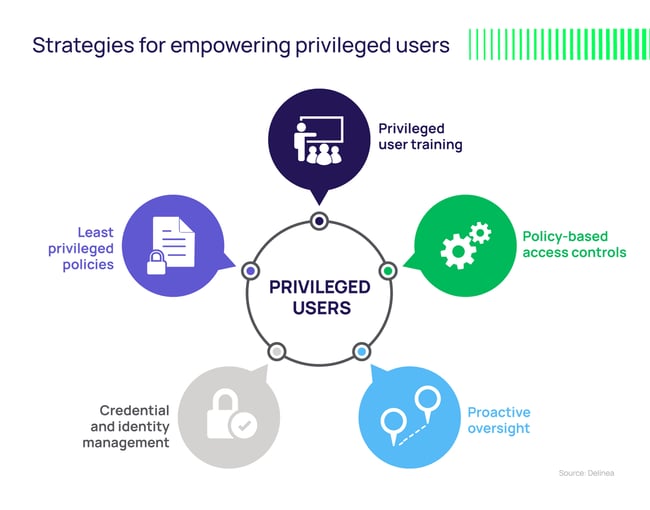
1. Privileged user training
Train employees to recognize suspicious behavior and give them ways to say something if they see something. This is especially important when people are faced with more sophisticated social engineering and phishing attacks, and with more personal devices used for business purposes.
Provide Privileged Access Management training to users who are accountable for privileged accounts. The training should emphasize the critical importance of privilege security and include security policies specific to your organization.
Get buy-in from your executive team by educating them as well.
2. Policy-based access controls
Implement a structured security process that details which types of privileged users and accounts should have access to which resources.
Share a formal policy to ensure accountability. Review and update it at least once a year, if not more often. Policies should be based on the categorization and classification of privileged user accounts specific to your organization.
Control new privileged user account creation with a formal review and approval process. The creation of any new privileged user account should be subject to specific reviews and approvals involving a peer or supervisor review.
Privileged account access should be limited by time, geographical location, the scope of permissions, and approval needed.
There are some accounts that privileged users might need access to for a limited time. Provide a mechanism for them to request “just in time” access to these accounts through privilege elevation, then revoke access automatically after a specified time has elapsed.
3. Proactive oversight
Actively monitor and routinely audit any privileged user accounts that have elevated permissions to spot illicit activity. If you suspect that a privileged user has been compromised, force authentication and/or automatically rotate credentials.
Deprovision or expire privileged user accounts that no longer require elevated permissions. This policy helps prevent what’s known as privileged access creep, where users accumulate privileges over time that may not still be required. Review and disable privileged accounts that aren’t appropriate for specific users—especially for accounts used by third-party contractors that are no longer needed.
4. Credential and identity management
Change default access credentials when setting up a new account, application, or system. One in five organizations has never changed default passwords, such as “admin” or “12345,” on privileged accounts.
Cybercriminals prioritize these default credentials because they’re so easy to crack. Automatically rotate passwords and force users to re-authenticate at times to expose any threat agent who is impersonating a legitimate privileged user.
5. Least privilege policies
While some users need more rights and responsibilities than regular users, sometimes they are over-privileged, which makes them a prime target for attackers. Enforce least privilege policies by setting all users to standard users and elevating their privileges only when necessary.
Privileged user management with PAM
By understanding the risks associated with privileged user accounts, you can put safeguards in place to ensure people can remain productive while also reducing risk. Privileged Access Management solutions help you proactively manage, monitor, and control privileged users and privileged account access.



