Privilege escalation on Windows: When you want it and when you don’t

Joseph Carson
Table of contents:
What is a privilege escalation attack?
Vertical and horizontal privilege escalation
Privilege escalation focuses on privileged accounts and access
How privileges are created and delegated in Windows system
Windows Security Identifiers
How do privilege escalation attacks work?
Step-by-step path to privilege escalation
Examples of privilege elevation techniques
How to automate privilege escalation
Privileged escalation attack paths with the Mitre ATT&CK framework
Top tips to make privilege escalation difficult for attackers
Privilege escalation is when a user with limited access to IT systems can increase the scope and scale of their access permissions. For trusted users, privilege escalation allows expanded access for a limited time to complete specific tasks. For example, users may need access to troubleshoot a technical problem, run a quarterly financial report, or install a program.
Privilege escalation is also one of the most common techniques attackers use to discover and exfiltrate sensitive, valuable data.
What is a privilege escalation attack?
A privilege escalation attack is a cyberattack that aims to gain unauthorized access into a system and attempt to access elevated rights, permissions, entitlements, or privileges. An attack can employ either vertical privilege escalation or horizontal privilege escalation to carry out the attack and ultimately gain access to high-value assets.
From a hacker’s perspective, privilege escalation is the art of increasing privileges from initial access, which is typically that of a standard user or application account, all the way up to administrator, root, or even full system access. With NT Authority\System access, attackers have full access to one system. With Domain Administrator access, they own the entire network.
An attacker may employ a variety of strategies to escalate privileges
Let’s say an attacker successfully steals a User’s password and gains access to their account. That password may enable certain privileges, for example, it may only unlock data stored locally on a laptop. But an attacker is hungry for more. They’re looking for more sensitive data they can resell on the Dark Web. They’re looking for access to business-critical systems so they can deploy ransomware, threaten shutdown, and demand financial payment.
To achieve those goals, an attacker employs a variety of strategies to escalate privileges:
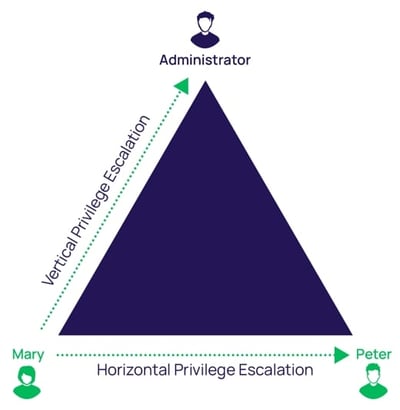
- Vertical privilege escalation, sometimes referred to as privilege elevation, is when an attacker compromises a user account that has limited permissions on a system. They then look for ways to increase their privileges using the same account. For example, they might add the compromised account to the local administrator group.
- Horizontal privilege escalation, the more common method, is when an attacker gains access to another credential on the network with higher privileges than the initial one used to gain their foothold. With higher-level privileges, an attacker can move freely around the network without detection.
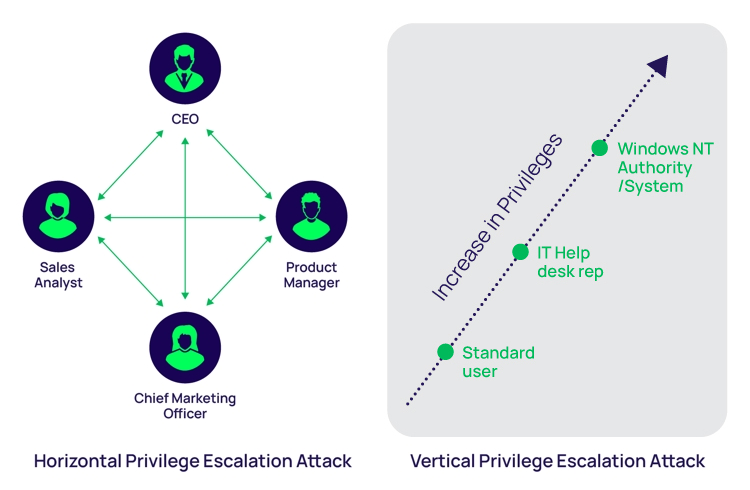
Examples illustrating the difference between vertical and horizontal privilege escalation
In this blog, you’ll learn how an attacker escalates privileges on Windows systems using a step-by-step process. By viewing privilege escalation through the lens of a hacker, you’ll see how attackers exploit security vulnerabilities to achieve their goals. And you’ll identify opportunities to increase Windows privilege management to reduce your risk of a cyberattack.
Here's an example of the elevation of a privilege attack using EternalBlue privilege escalation exploit:

Example of when an attacker has pwned a system with NT Authority\System
Privilege escalation focuses on privileged accounts and access
Before we start getting into the mechanics of Windows privilege escalation attacks, we must first understand what privileged accounts are used for, the different types of privileges on Windows systems, and how they work. This foundation will help you understand the strategies cyber criminals use when attacking Windows systems so you know where to focus your defenses.
Privileged accounts are at the core of every business. They ensure the IT team can manage the organization’s systems, infrastructure, and software, and they enable employees to access the data that enables them to make critical business decisions.
Privileged accounts are distinguished from standard User accounts that represent human identities, such as an Active Directory User account with a password to restrict access.
Privileged accounts enable administrative or specialized levels of access based on higher levels of authorization. It’s common to have shared privileged access used by a department or group of Users to access applications or systems. A privileged account can be human or non-human. Some types of non-human high privileged accounts are application accounts used to run services requiring specific permissions.
Privileged accounts allow Users to make system and software configuration changes, execute administrative tasks, create and modify accounts, deploy software, back up data, install security patches, enable interactive logins, and of course, access privileged data. All these activities are crucial to ensure a business can function by keeping systems and software running.
How privileges are created and delegated in Windows systems
A privilege in Windows operating systems is the authorization delegated to a User account or Group that allows access to system resources, objects, and tasks. Privileges can be Local or Domain, which determines the scope of access the User account has.
On Windows systems, you can find a list of Local User Accounts under Local Users and Groups in the computer management menu. Administrator, Default, and Guest are default accounts.
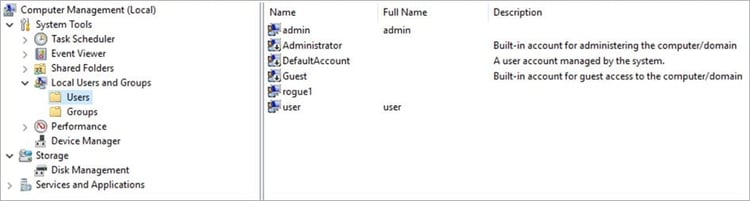
Computer Management Local Users and Groups
A Local User account can be assigned as a member of a Group, which determines its privileges.
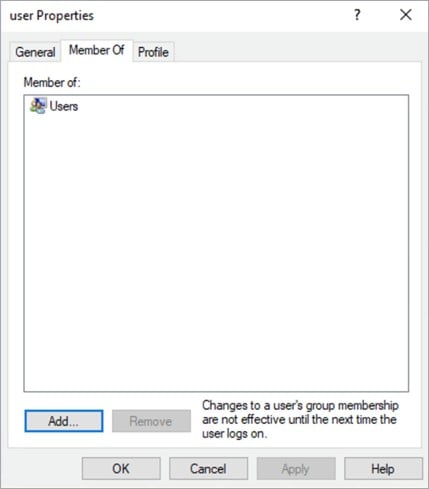
User account properties showing it is a member of the Users Group
Default Groups on a Windows system depend on the operating system role and features enabled. Groups tend to be focused on roles or tasks that the User will perform based on their job function.
Unfortunately, many organizations rely on out-of-the-box roles. When unsure which role to assign to Users, most delegate Local Administrator privileges. This results in many overprivileged Users, which attackers search for and quickly abuse.
Each Windows system has its own Security Account Manager database, known as the SAM file, which stores User accounts and security descriptors on the local computer. When a User logs onto the system, they access a token that contains privileges. When they perform any action on the system, it checks if those permissions permit the action.
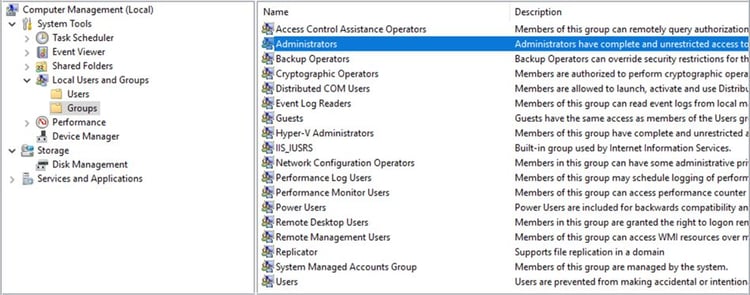
A few default Groups that determine the privileges of users
Typically, when a User doesn’t have permissions to an object within Windows, they’ll be prompted to enter a different User account with the necessary privileges. This is commonly known as User Account Control (UAC) and enables a User to run most tasks as a non-Administrator.
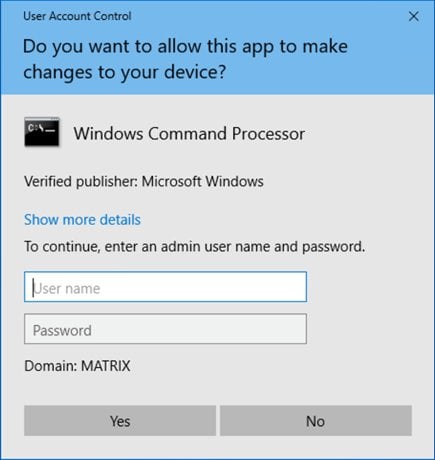
User Account Control requiring elevated privileges to run cmd application
Once the Users and Groups have been assigned and configured, security settings are determined and privileges are assigned to each Object, such as file systems, registries, services, and system resources. In a hierarchy, each Object can inherit permissions and privileges from its parent.
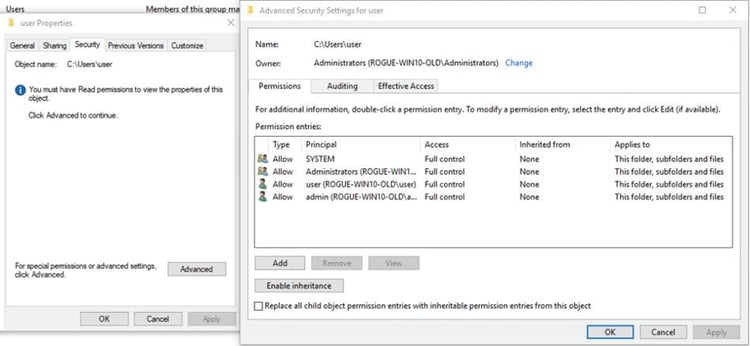
Common Security Settings aka ACL for an Object in Windows
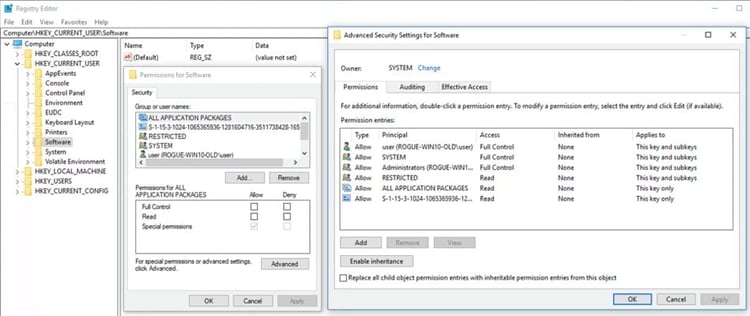
Example of permissions aka ACL within the registry
Windows Security Identifiers (SID)
In Windows, the SID is how the operating system refers to accounts and processes instead of using an account or process name.
Each account, Group, and process, is assigned a unique SID (Security Identifier) to represent the security context it’s running under. When a User logs onto a system or executes a process, the SID is assigned an access token that contains everything the system needs to determine the security context, permissions, privileges, Groups, and access.
To check the User account’s SID, you can use the WMIC (Windows Management Instrumentation Command-Line Utility). Use the command prompt: wmic useraccount get name,sid.
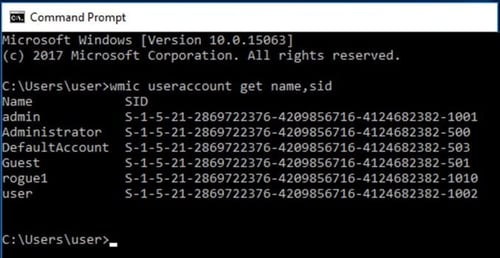
An Example of User Account SIDs
To learn more about SIDs, I recommend reading Microsoft’s full documentation which can be found here:
Microsoft Security Identifiers Documentation
Did you catch the security concerns?
We've now covered the ways privileges are created and assigned in Windows. That’s the “happy path,” in which everything works out according to plan. But, even if you follow all of the steps outlined above to manage privileges, you’re leaving yourself open to a privilege escalation attack.
Next, we’ll cover the “unhappy path.” That’s when a cyber attacker targets your Windows privileged accounts and successfully exploits the security holes.
Privilege escalation attacks and exploit techniques
For hackers, privilege escalation is the art of elevating privileges from initial access (typically, standard User or application account) to Administrator, root, or even full system access, on Windows referred to as NT Authority\System.
How do privilege escalation attacks work?
To target privileged accounts, attackers use common steps and proven techniques to identify system misconfigurations, vulnerabilities, overprivileged Users, and weak credentials.
First, they explore systems to determine an attack path that won’t alert the security team that anything malicious is occurring. They’re looking for privileged accounts which are left unmanaged and unmonitored.
Some of the most common privileged accounts that attackers go after include:
- The King of Accounts “Domain Admin Accounts”
- The challenging and scary “Domain Service Accounts”
- The forgotten “Local Administrator Accounts”
- The help me “Emergency Accounts”
- The hidden and forever “Service Accounts”
- The elevated “Application Accounts”
- The silent but deadly “Privileged Data User Accounts”
You can learn more about these types of accounts in the blog: The 7 Deadly Privileged Accounts You MUST Discover, Manage, and Secure.
Step-by-step path to privilege escalation
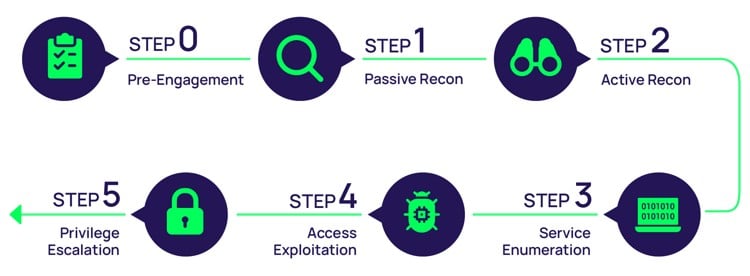
Example of the steps an attacker will take
Let’s assume the attacker has gained an initial foothold on a Windows system. The initial foothold could mean different things, such as a reverse shell (aka without creds), access to an application running on the system, or creds (credentials) of an account with limited privileges, such as a standard user account. Each type of foothold allows the attacker to begin their privilege escalation attack path.
In a privilege escalation exploit, the attacker commonly seeks to discover as much as possible about an IT environment to determine their attack path. They do this through reconnaissance and enumeration of the compromised systems.
They perform some type of system enumeration using commands like the ones below:
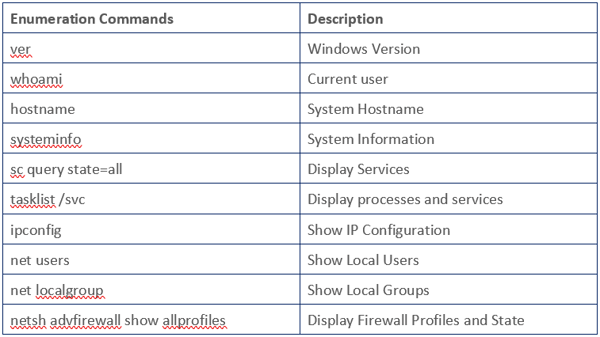
Operator Handbook by NETMUX is a great book that includes many enumeration commands and tips. This book has an awesome collection of steps to enumerate a system.
Below is an example of these enumeration commands in action:

Manual Enumeration
Examples of privilege elevation techniques
When performing enumeration, attackers are looking for security vulnerabilities that allow for privilege escalation exploits, such as:
1. Insecure service permissions
This occurs when a service that's running under SYSTEM privileges, but the User has permissions to change the executable binpath to one which could create a reverse shell.
2. Unquoted service paths
Surprisingly, while this is a known technique used for many years, it’s still common to find many services with unquoted service paths. When combined with weak folder permissions, this allows an attacker to place an executable in a parent folder, where Windows will look for the executable first to execute. For example, you might have a service path as C:\Program Files\Vendor\binary.exe. When the path is unquoted and the User has permissions to place objects in the C:\Program Files\ path, Windows will first try to execute program.exe. If the attacker can place a binary called program.exe in the path, they can then elevate privileges to the account which that service is running.
3. Weak registry permissions
Like the insecure service permissions example, if an attacker can modify the registry configuration of a service, they can then change the path in service configuration to execute a binary they choose. This could create a reverse shell or elevate privileges on the system.
4. Insecure service executables
If an attacker can simply replace the original executable with their own, they can then gain privilege escalation of the account which that service is running under.
5. Passwords
I can’t tell you how many times I’ve found passwords for privileged users sitting in a text file on a desktop, in a browser, or in a configuration file. Even today, when many people know that passwords are a top attack target, it’s still common to store passwords in easy-to-find places. Many people create weak, crackable passwords, reuse them, and share them.
Attackers can quickly search for stored passwords using the common techniques, such as:
Searching the registry using the query: reg query HKLM /f password /t REG_SZ /s
Searching the file system within xml, ini and txt files for the string password: findstr /si password *.xml *.ini *.txt
Finding a text file on the desktop labeled something like “passwords,” or “important stuff.”
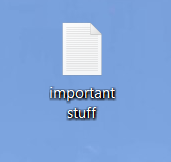
Identifying stored passwords in an internet browser:
6. Overprivileged Users
For example, standard business Users may have Local Administrator rights on their personal workstations. Attackers can leverage these Local Administrator rights to escalate privileges up to Full Domain using tools such as mimikatz and changes in the OS configuration. You can see how this privilege escalation strategy progresses in the 3-minute video.
7. Security Account Manager (SAM)
Windows stores credentials within the Security Account Management (SAM) database in an encrypted form called a hash. This is a one-directional cryptographic algorithm, which means you need to know the original password to recreate the hash. The SAM and SYSTEM files are locked when Windows is running, but an attacker might find a backup copy under the Windows repair directory.
Getting access to both the SYSTEM and SAM database could allow an attacker to extract the hashes. If the original password was a weak, reused password, it’s very likely the attacker can crack it. Here's an example of cracking a hash using Hashcat.
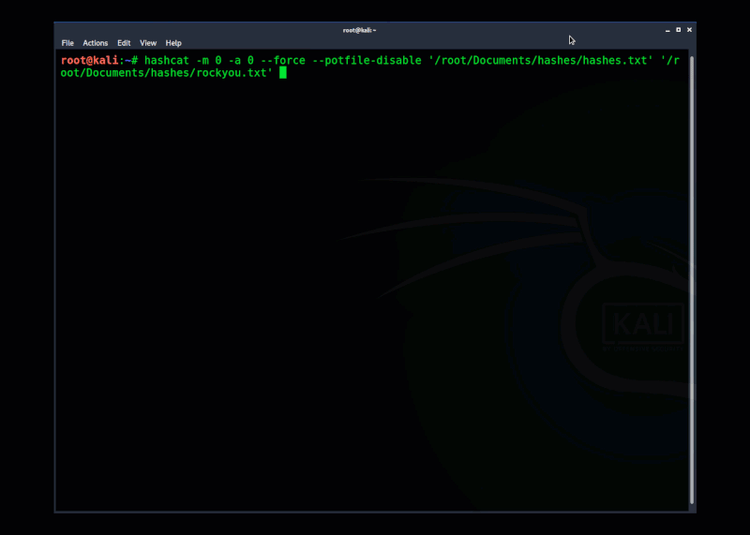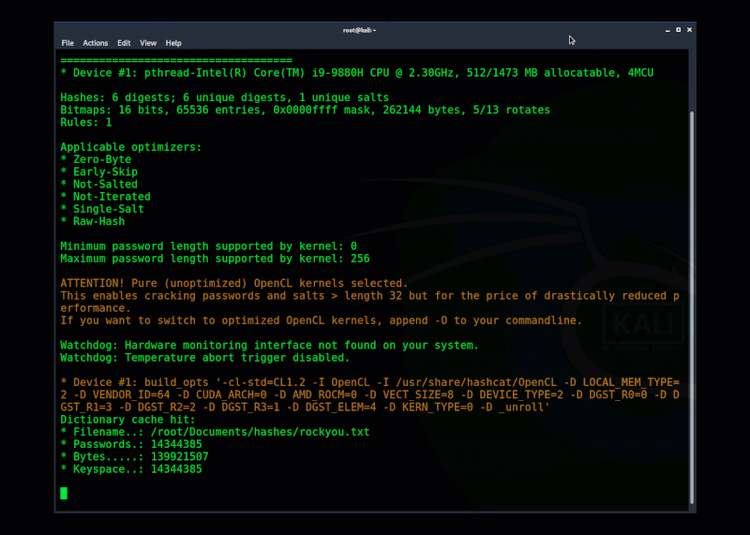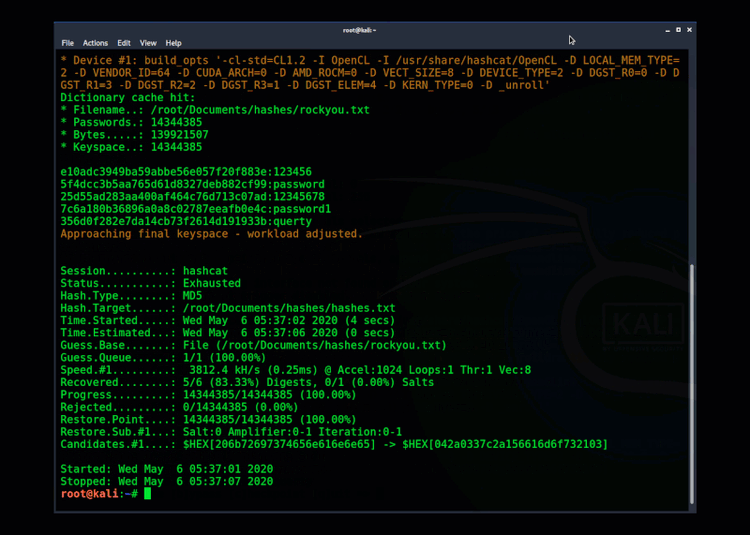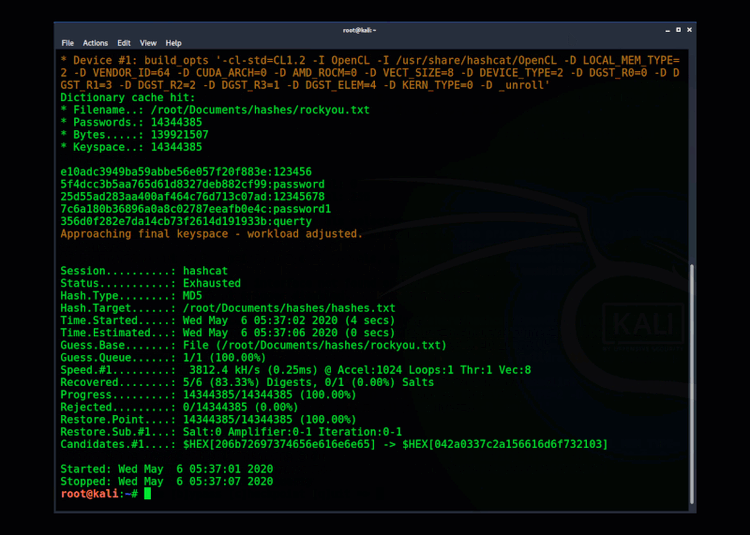
Example" Using Hashcat to crack hashes
8. Pass-the-hash
If an attacker can’t crack the password from the hash, they may still be able to move around the network using only the hash. This technique is called pass-the-hash. An example of privilege escalation using pass-the-hash for lateral movement is below:
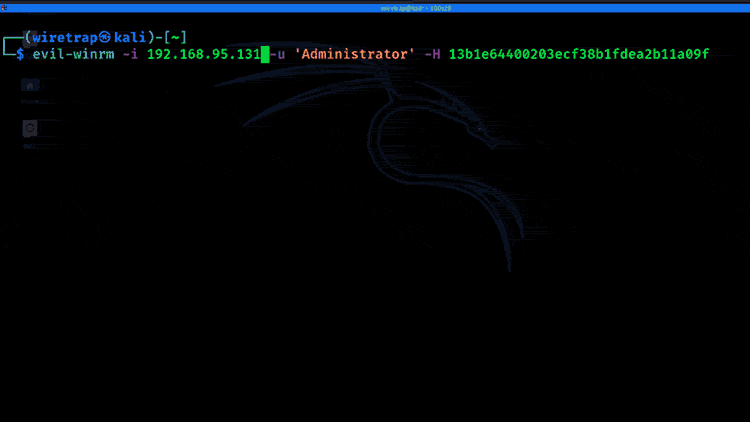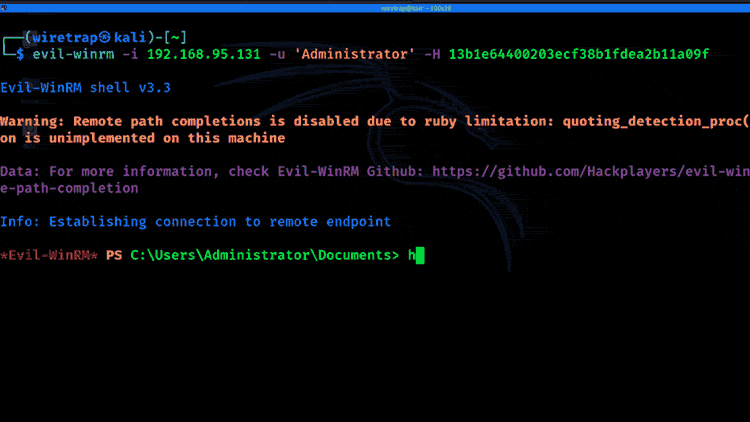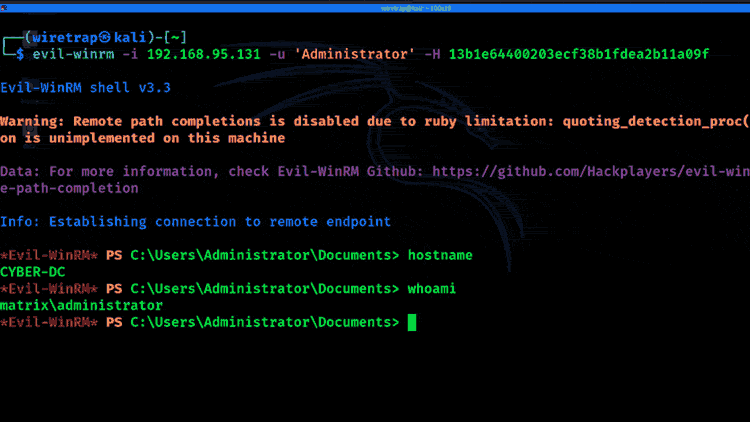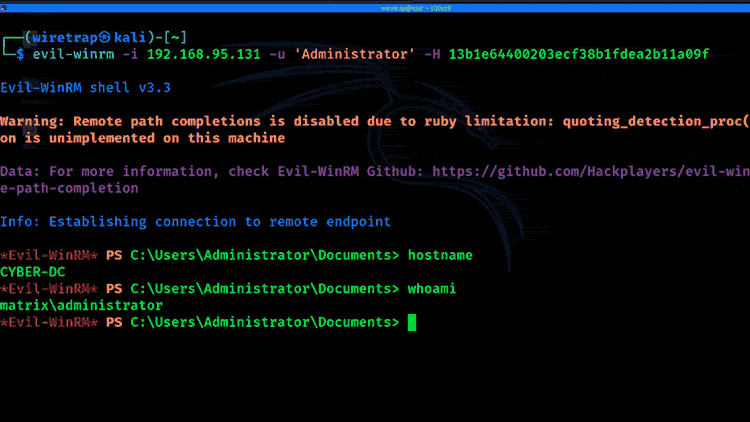
9. Insecure GUI apps
For example, a recent vulnerability in a Razer Mouse software enabled a User who plugs in a mouse to escalate privileges to a Windows 10 Administrator. Once the mouse was plugged in, a Windows update would launch, downloading the Razer Installer as SYSTEM. A User could then use Explorer to launch an elevated PowerShell window. An example of privilege escalation using insecure GUI Apps is below.
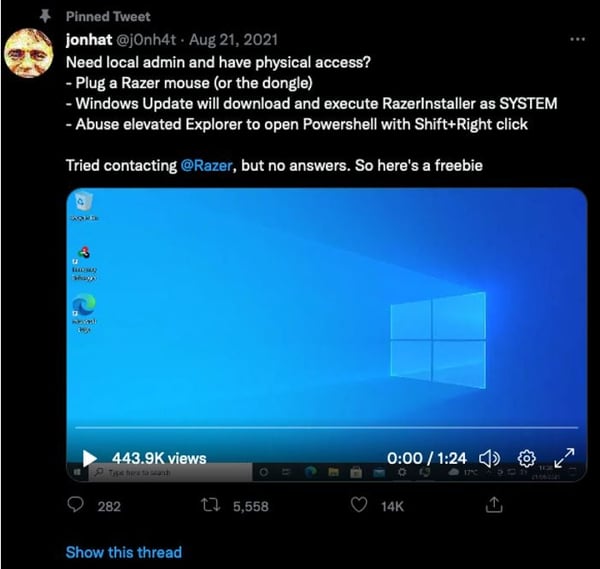
View the Insecure GUI App example on Twitter
10. OS vulnerabilities or kernel exploits
While these types of escalation attacks are less common, sometimes attackers will wait for months with access to a low privileged User, waiting for the moment a vulnerability is disclosed. A recent example known as Print Nightmare (CVE 2021 34527) is a vulnerability in the Print Spooler that enabled an attacker to perform remote code execution and privilege escalation.
An example of privilege escalation using Print Nightmare to create an Admin User on the system is below:
Example: Exploiting Print Nightmare CVE 2021 34527
How to automate privilege escalation
A hacker wants to escalate privileges as quickly as possible to avoid detection. Therefore, they may use tools to automate the privilege escalation process, such as the examples below:
BloodHound
BloodHound is a single-page Javascript web application, built on top of Linkurious, compiled with Electron, with a Neo4j database fed by a C# data collector. It uses graph theory to reveal hidden and often unintended relationships within an Active Directory environment.
Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to find. Defenders can use BloodHound to identify and eliminate those same paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory environment. An example of an Active Directory privilege escalation attack is below, using Bloodhound to find the attack path to elevation of privileges.
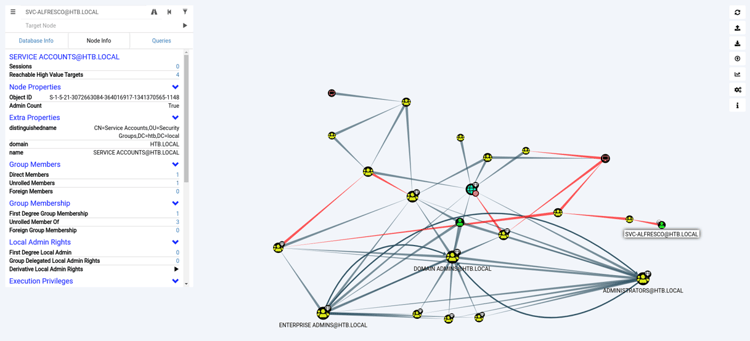
Bloodhound example from Hackthebox
Windows Exploit Suggester—Next Generation (WES-NG)
WES-NG is a tool based on the output of Windows’ systeminfo utility. It provides the list of vulnerabilities the OS is vulnerable to, including any exploits for these vulnerabilities. Every Windows OS between Windows XP and Windows 10, including their Windows Server counterparts, is supported.
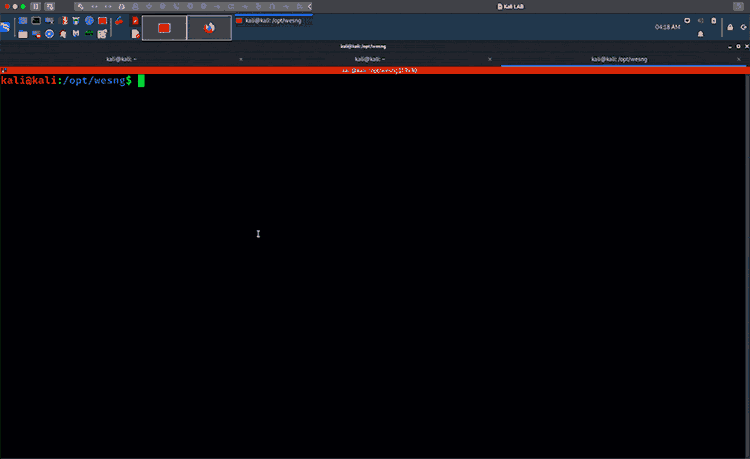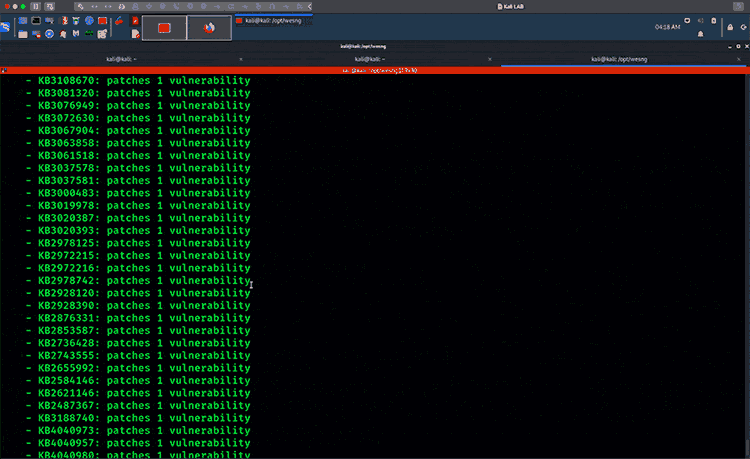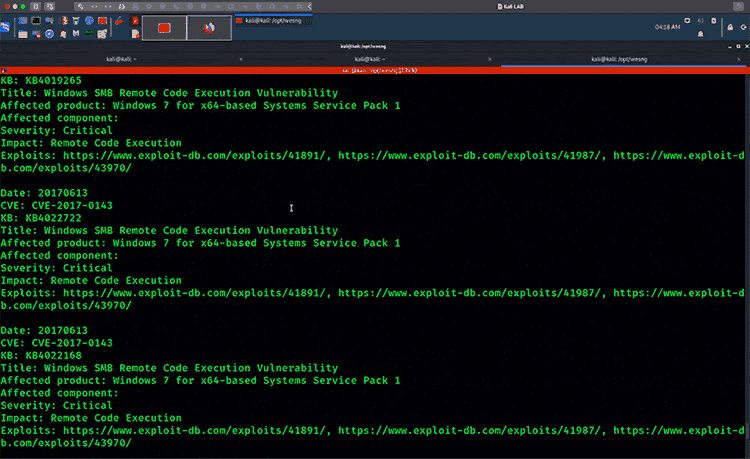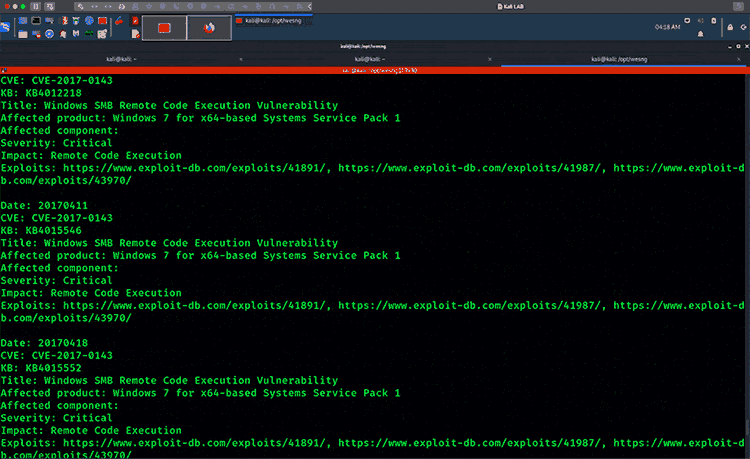
WES-NG running against Windows 10 System Info
Windows Privilege Escalation Awesome Scripts
Using winPEAS can help Administrators look for ways to prevent privilege escalation attacks by assessing systems for possible misconfigurations or vulnerabilities. WinPEAS is a compilation of local Windows privilege escalation scripts to check for cached credentials, user accounts, access controls, interesting files, registry permissions, service accounts, patch levels, and more. WinPEAS is helpful because it includes hints on where you should focus your attention.

WinPEAS running on Windows 10 endpoint
We recently had the awesome Carlos Polop, author of winPEAS and Hacktricks.xyz, on the 401 Access Denied podcast to discuss winPEAS and privilege escalation. Make sure to check out the podcast and Carlos’s Hacktricks book, as it goes into full detail on many of the techniques used in this blog.
PowerUp
PowerUp is a collection of PowerShell scripts for finding common Windows privilege escalation vectors that rely on misconfigurations. Running Invoke-All checks will look for common misconfigurations on Windows endpoints.
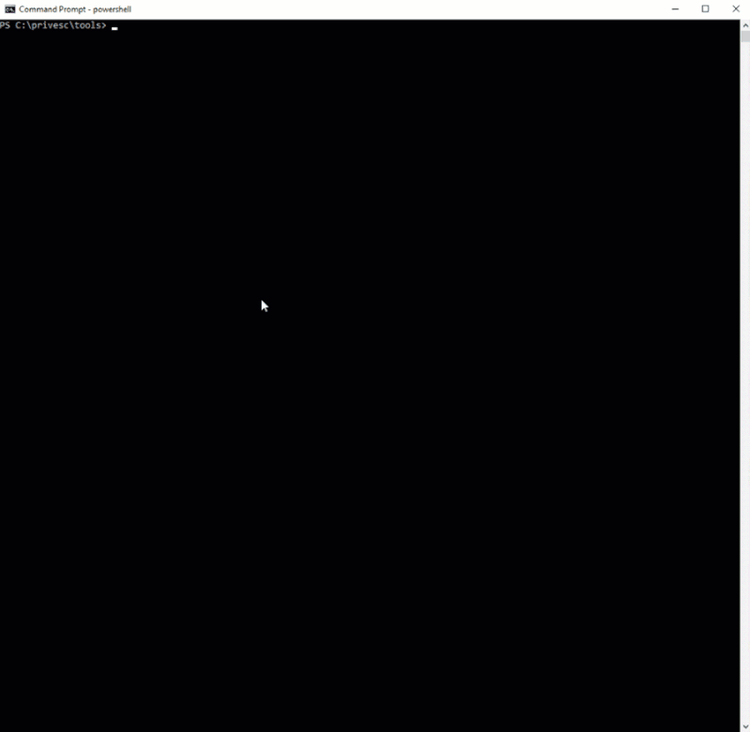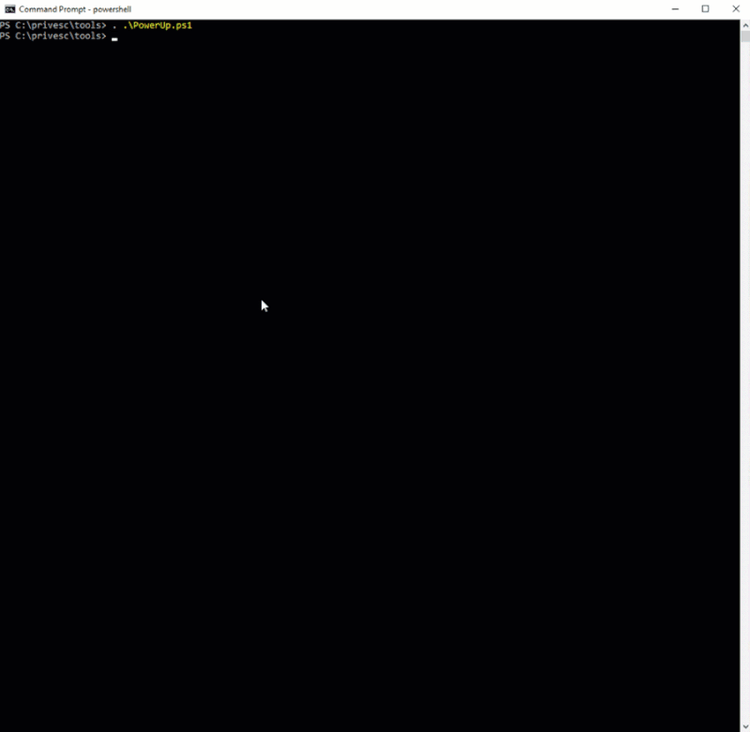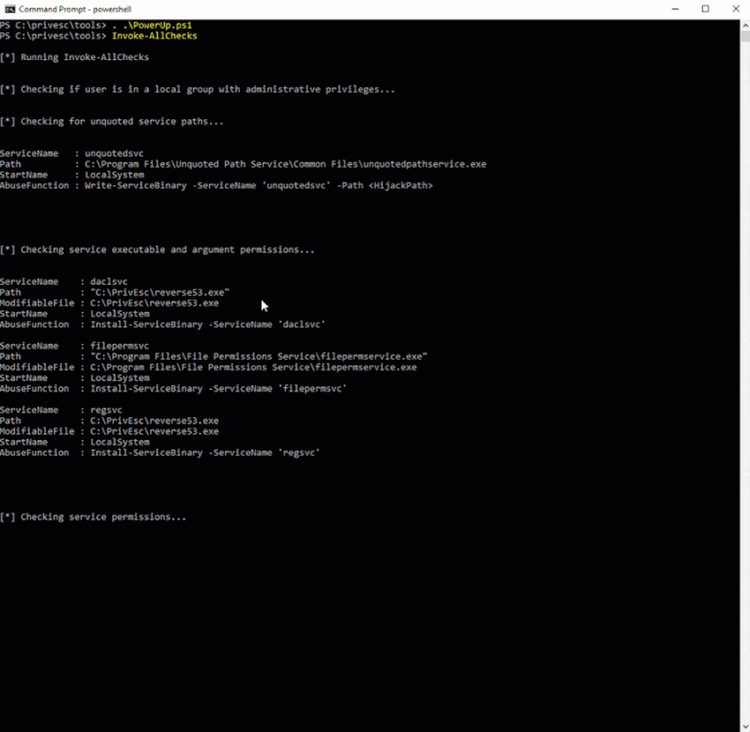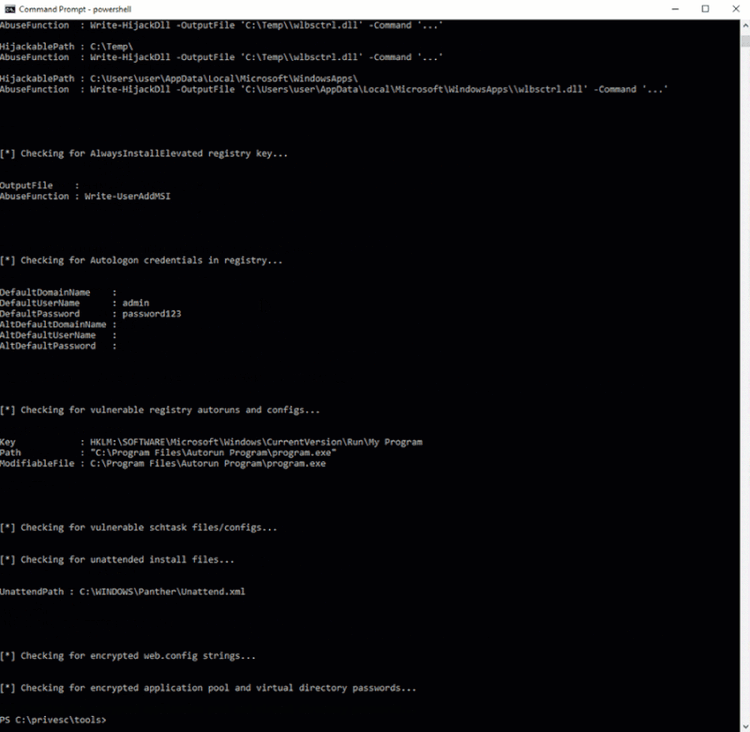
PowerUp running on Windows Endpoint
Seatbelt
Seatbelt is a C# project that performs security-oriented host-survey “safety checks” relevant from both offensive and defensive security perspectives. Simply, Seatbelt is an enumeration tool to show information that could lead to privilege escalation.
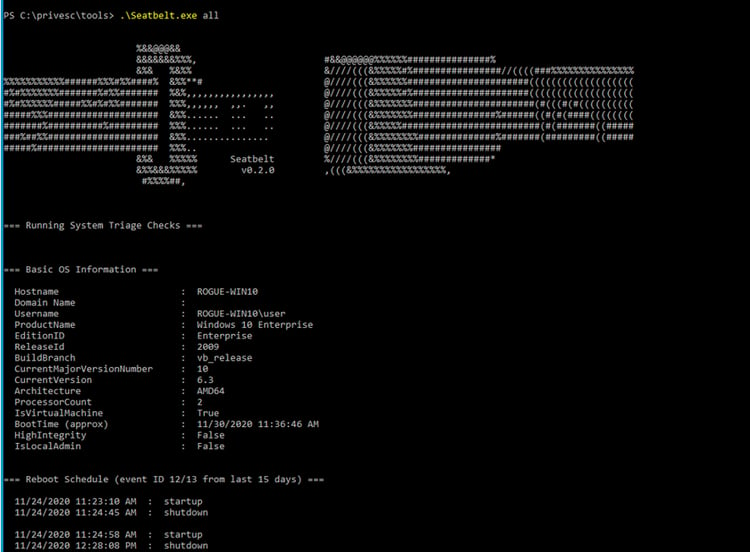
Seatbelt running on Windows endpoint
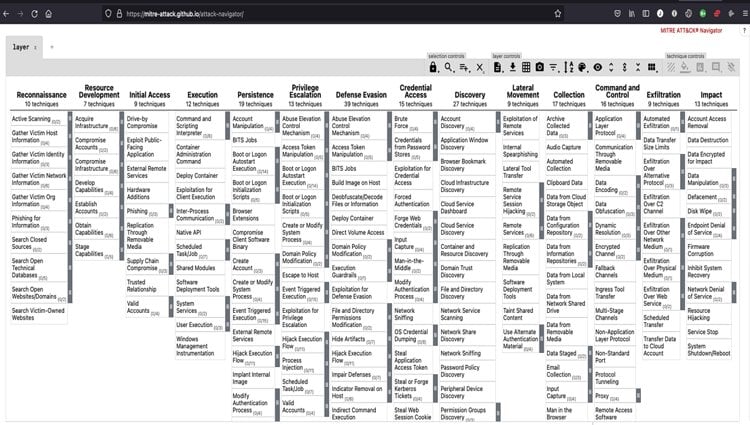
Privileged escalation attack paths with the Mitre ATT&CK framework
The Mitre ATT&CK framework is a tremendous knowledge base of the common tactics and techniques used in real-world attacks. Knowing the techniques and how to reduce risk is critical to making your organization resilient against cyberattacks.
Mitre ATT&CK Framework Privilege Escalation
Top tips to make privilege escalation difficult for attackers
Now that we’ve covered the common attack strategies cybercriminals use to escalate privileges, let’s dig into the defense strategies you can use to protect your organization.
It’s dangerous to assume anyone can definitively prevent privilege escalation attacks
First, let’s address the word “prevent.” It’s dangerous to assume anyone can definitively prevent privilege escalation attacks. In fact, assuming that you can prevent can lead to a false sense of security. Instead, we can reduce risks, we can make it more difficult for attackers to be successful, and we can increase visibility to stop the progression of exploits.
Therefore, it’s important to harden your Windows systems as much as possible, forcing attackers to use more noisy techniques that raise alarms. The earlier you get the warning signs, the better your chance of preventing a catastrophe.
Here are some best practices to make privilege escalation exploits harder for attackers:
1. Move passwords into the background using an enterprise password manager or Privileged Access Management (PAM) solution
Help users avoid making poor security decisions by helping them move passwords into secure vaults so they aren’t easily found by attackers during the enumeration phase. A strong password manager or PAM solution will help avoid passwords being left on the desktop in clear text, hidden in configuration files, or stored in insecure browsers.
With a PAM solution, you can ensure all services have a provisioned account with the correct security controls, including complex passwords, rotated frequently. Throw universal keys and standing privileges away and move to on-demand, just-in-time privileges.
Learn more in our whitepaper: Invisible PAM: Balance Productivity and Security Seamlessly
2. Remove local administrator privileges and practice the Principle of Least Privilege
We’ve all heard about Zero Trust. But, how do you put those strategies into practice? The best place to start is moving to non-persistent privileges or least standing privileges, which means a user or account should have just enough privileges to perform the task or action they are assigned to do. This reduces the possibility of exposing several of the privilege escalation paths described above, such as insecure services, registry, and directory paths.
3. Implement MFA everywhere
Passwords are one of the most common targets, so let’s not leave them as the only security control to critical systems, applications, or privileges.
Rather, make sure to add security controls such as Multi-Factor Authentication, access workflows, and approvals, to ensure that only authorized users can use privileges even when an attacker compromises the password. MFA should be required not only at system log-in, but also at the point of horizontal and vertical privilege elevation.
4. Implement application control
Limit the ability to run applications and scripts that can be used to enumerate or exploit privileges. Approval lists control which applications and scripts can execute. Deny lists control which known malicious applications and scripts are blocked or require additional auditing.
5. Patch and update systems and applications
It’s not 100% protection, but it certainly makes the attacker’s goal of privilege attack and escalation more difficult.
6. Audit and log all privilege access usage
Make sure to monitor privilege usage for abuse and suspicious activity. Set alerts to ensure you have visibility and can investigate when something suspicious occurs. Should a privilege escalation exploit occur, you’ll be able to conduct incident response and identify the root cause of the attack to prevent it from happening again.
Looking for more advice on defending against privilege escalation attacks?
We’ve covered a basic explanation of privileges in Windows and foundational techniques and security controls to combat privilege escalation attacks. Privilege escalation defense does get more complicated when we start looking into Active Directory, cloud environments, and Single-Sign-On.
If you’re looking for more detail on privilege escalation techniques on Active Directory, I recommend reading our whitepaper: