How to protect service accounts without losing your mind: Automated tools!

Barbara Hoffman
Here at Delinea, we are always banging the drum on the importance of securing privileged access. We got a glimpse of what can happen if you don’t when more than 100 million credit applications at Capital One were stolen by an individual in a security breach that involved a web service and compromised privileged account. The attacker apparently got into the network through a misconfigured firewall, extracted privileged account credentials, and used them to access sensitive information and eventually download/steal credit card application data without being detected until after the damage was done.
Here’s the problem: Many recent high-profile breaches have one thing in common—they were accomplished through the compromise of privileged credentials. Industry analysts estimate that up to 80% of all security breaches involve the compromise of privileged accounts. Virtually all organizations have some unknown or unmanaged privileged accounts. Some may have thousands. These accounts increase an organization’s vulnerability and present an opportunity for intrusion.
Skip the service account info and go straight to the 5 Best Practices.
Service accounts are often the most commonly neglected
Of these unmanaged accounts, service accounts are often the most commonly neglected. Service accounts are privileged accounts that proliferate throughout every organization, running in the background, accessing applications and IT services critical to business operations. They are specialized “non-human” accounts typically used within operating systems to execute applications or other services accessing data and network resources to perform specific tasks. As such, service accounts often operate with specific local system privileges needed to function and/or to connect with other network resources. That means service accounts usually have elevated privileges and access to business-critical applications and data.
Outsmart Cybercriminals
When IT teams fail to properly manage these accounts, it leads to significant cybersecurity risks. That’s especially true for mid-size and enterprise organizations that use Active Directory. At that size and scale, service accounts become too numerous to be managed manually, leaving them vulnerable to compromise and exploitation.
If a single privileged account is used across an organization to run many services or applications, when that account is breached, your risk increases exponentially. It only takes one compromised account for an attacker to gain access to virtually any information within your organization’s IT network.
Service account sprawl is associated with some bad security habits
There are several reasons why service accounts can get out of control and end up putting companies at risk of a compromise.
Typically, IT admins are too busy or lack the proper mechanisms to properly record why a specific service account exists. So it’s not surprising that IT managers don’t know which users have access, what services depend on it, or when it should be disabled or deprovisioned.
Service accounts are often neglected because updating or changing credentials is risky. Any changes can affect running services within a chain of dependencies, causing unforeseen disruptions. It’s difficult, if not impossible for many, to map and keep track of business services that rely on these accounts. Of course, no one wants to be responsible for an “unnecessary” outage.
Former employees or consultants can remember service account credentials and reuse them for other companies
In addition, former employees or consultants can remember service account credentials and reuse them for other companies. These credentials are no longer unique and possibly already exposed. Even worse, they could be abused for unauthorized access.
With limited options for managing service accounts, many organizations have developed poor security credential practices such as:
- Giving excessive privileges, or overprivileged service accounts
- Failing to rotate or change service account passwords
- Leaving default passwords in place
- Using the same account for multiple services
- Using poor service account naming conventions
- Sharing an account between services and people
- Using the same password for multiple accounts
- Never decommissioning service accounts when they are no longer needed
The cybersecurity risks are real
In a 2019 Black Hat Survey Report conducted by Delinea, cybercriminals and security professionals were asked about current practices and risks associated with service accounts. 24% of security professionals said service accounts were their most vulnerable targets for attacks by cybercriminals.
According to the survey, service accounts are such an attractive target because they can provide:
- Easily elevated privileges
- Access to valuable/sensitive data
- Persistent access allowing under-the-radar movement across the IT environment
Turning a blind eye to service account password best practices?
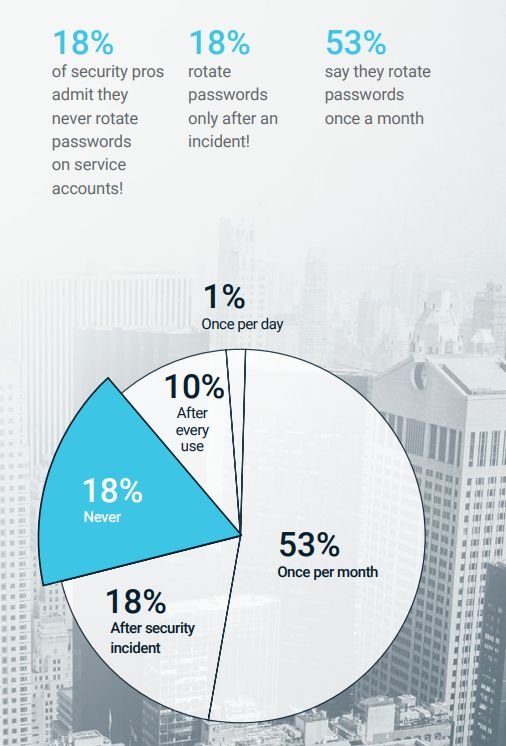
Unfortunately, service account password security is seriously lacking. According to the survey, 18% of security professionals admit they never change service account passwords, and another 18% only change passwords after a security incident. That’s more than one out of three service accounts that are highly vulnerable.
Getting control of service account sprawl
Almost all large organizations suffer from extreme service account sprawl, perpetuating the unmanaged, uncontrolled expansion of their privileged account attack surface. That’s why we published our eBook “Service Account Security For Dummies.” It was written to help our customers get control of their numerous service accounts and manage them more effectively.
So, how do you get there? Here are five service account best practices designed to help you manage and safeguard your service accounts from neglect, abuse, or exploitation.
1. Discover your service accounts
How can you protect your service accounts if you don’t know where they are? All too often I hear from companies that the biggest barrier to protecting these accounts is fundamentally just not knowing where they are, or how many exist. IT teams are aware they may have these “backdoor accounts” that allow users and cybercriminals to bypass proper controls and auditing in order to compromise these accounts. They also know malicious insiders can create service accounts to gain access to sensitive information and go undetected for months or even years. But they feel powerless because they can’t discover and/or continuously identify service accounts. There are simply not enough resources to manage it properly with manual methods.
Delinea has a free tool to get you started in your discovery process. Delinea’s Service Account Discovery Tool measures the state of privileged access entitlements in Active Directory service accounts and exposes areas of highest concern. After running the Discovery Tool you receive a customized, prioritized risk report you can download and share.
Delinea has many free tools like the one mentioned above—you'll find them here: Our top 15 PAM Tools.
2. Document, classify, and inventory your service accounts
Very few organizations have the time, tools, or inclination to inventory their service accounts. As a result, many service accounts may exist without any oversight or accountability. In light of recent events involving the compromise of these accounts, IT teams need to create a record that explains why accounts exist, which humans have credentials to access them, and which service(s) depend on each service account. And don’t forget to include when the service account should be reviewed, deactivated, or deleted.
Look for advanced solutions that can automate the process of finding unmanaged and unknown accounts. This can greatly alleviate the amount of time and resources required to document, classify and inventory service accounts.
3. Secure access to each service account
As with any privileged account, customized credentials must be associated with each service account. You should already have them in a centralized vault, and credentials should be limited only to necessary access. When you first discover a service account, for example, change passwords immediately and put it on a rotation schedule along with a way to monitor and ensure someone else hasn’t gained access or changed credentials outside the system. You’ve got to use an automated privilege access management (PAM) solution to accomplish this effectively and efficiently.
Keep in mind that not all service accounts use passwords; some are set to the system and some use SSL Keys, which are a commonly used means of authentication within enterprise IT environments. Because of a lack of visibility, IT groups often overlook these credentials when building a privileged access security strategy.
4. Establish governance and assign accountability
Over the long term, you must implement a governance plan for managing your service accounts. Your plan has to assign ownership to individual users and build a role-based permission system that encompasses administrators, requesters, owners, and approvers.
Companies should standardize when service accounts are created in accordance with their company’s security policies. When setting up an account, it is critical to determine which organizational or business unit the service account should be assigned to and any other AD attributes required.
Establish a workflow for requesting service account creation and the proper approval steps, along with a process for assigning account ownership. An individual IT manager, a business owner, IT admin, or a security staffer should be clearly designated as responsible for approving new account creation.
There is an excellent report from analyst firm KuppingerCole called “Privileged Access Governance” that will help you understand how to govern non-human service accounts and prevent insecure service account sprawl. It explains in depth how a new generation of automated Privileged Access Governance solutions can help you achieve and maintain service account control and security.
5. Automate service account governance (and keep your sanity)
When seeking to automate service account security from provisioning through decommissioning, answer several questions upfront. Your responses will confirm the requirements you need and want from any automated solution. For example:
- Who in your organization should be involved in the creation, approval, and ongoing management of service accounts?
- How often should the service account be reviewed? We recommend setting this according to internal policies and/or compliance requirements.
- If the account is renewable, can the account owner do it themselves or should the renewal go through the same approval process as when it was first created?
- In Active Directory, there are options for decommissioning an account. Do you want it to be disabled, expired, or deleted?
- What are the appropriate steps when you want to decommission a service account? Do you want the service account owner to do it or can a policy-guided tool do it automatically?
Once you’ve assessed your service account environment, you can effectively evaluate automated security tools. Here is a handy checklist that covers the functionality you need to implement proper governance to achieve the outcomes outlined above successfully.
- Establish workflow
Look for an automated tool that will help you establish processes for tighter control over service accounts. Start with workflow templates that support the process and policies outlined above. Get familiar with the tool and then apply customizations to provide more in-depth visibility and control that supports your security objectives.
- Delegate ownership
Delegate ownership with role-based permissions that govern the user access, request, and set up workflow. Select automated tools that empower you to create users, groups, and roles aligned to the needs of your business and security policies.
- Provision service accounts
Once a process has been put in place, provisioning really is the first critical step in taking control of service accounts. Look for tools that allow you to provision service accounts seamlessly and automatically. Admins should be able to define workflows for the provisioning process by setting required approvals for each type of service account request.
- Enforce governance
An effective automated tool should allow you to enforce governance with designated accountability and ownership over every service account. According to analyst KuppingerCole “Privileged Access Governance promises the necessary control over privileged account lifecycle events and visibility into their access patterns and associated risks.” Basically, what this requires is that IT teams have the automated tools and mechanisms to enforce the workflows, ownership, and controls described in the sections above.
- Decommission accounts
To reduce sprawl and reduce the privileged account attack surface, you must decommission unneeded accounts automatically without causing disruption. You should be able to trigger notifications when accounts should be renewed, reapproved, or even deleted. Decommissioning is more than simply deprovisioning. You may want to review, disable, expire, or delete/deprovision service accounts.
Free Trial of Delinea’s Account Lifecycle Manager
Delinea’s Account Lifecycle Manager is a solution that automates and streamlines the full privileged account lifecycle of service accounts, finally enabling you to control service account sprawl. Now you can easily secure, provision, and decommission service accounts to harden and ultimately reduce your attack surface with Account Lifecycle Manager. The free trial below includes the full version of Account Lifecycle Manager, with all features enabled and access for 10 users, for 30 days.
Account Lifecycle Manager



