How to Become the Master of Your PAM Journey

Barbara Hoffman
If you’re just getting started with PAM—Privileged Access Management —you’ll want to check out Delinea’s PAM Maturity Model. The model is a framework to help you set the right PAM foundation and get your organization on the PAM journey, now and in the future.
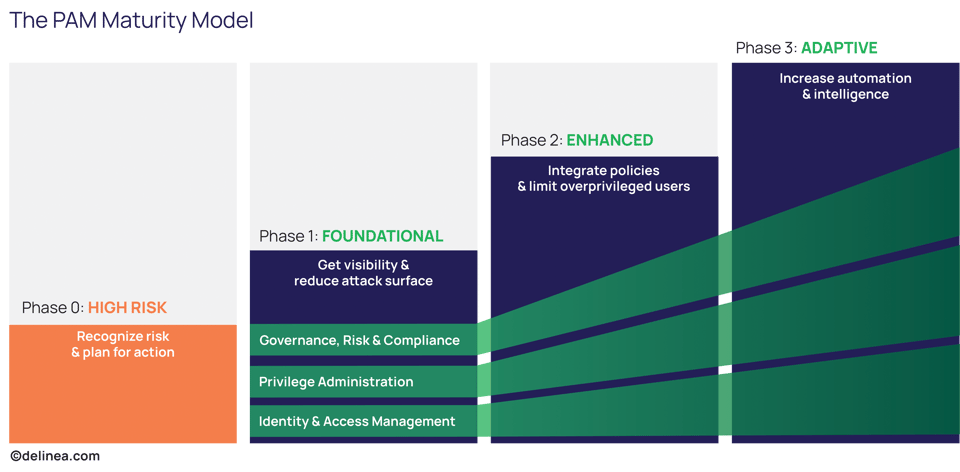
It’s based on security industry best practices and Delinea’s work with over 10,000 customers of all types, ranging from organizations just beginning their PAM journey to the most experienced and advanced PAM users. First, you’ll need a basic understanding of how PAM works.
So, how does Privileged Access Management work?
- A user needs to access sensitive info to perform a task
- The user must request access and justify the purpose
- The PAM solution approves or denies access, depending on how it's set up
- User is given appropriate access, usually without ever seeing the organization's password
Now that you know how PAM works, take a look at Delinea's PAM Maturity Model
The PAM Maturity model defines four phases of PAM maturity:
- Phase 0: High Risk
- Phase 1: Foundational
- Phase 2: Enhanced
- Phase 3: Adaptive
Each maturity phase is characterized by an organization’s approach to PAM across three dimensions:
- Governance, Risk, and Compliance (GRC) – How strong is the integrity of your system, and how much visibility and oversight do you have?
- Privileged Administration – How do you create, define, and manage privileges across your organization?
- Identity and Access Management – How strong are your authorization controls and how granular are your access controls?
As organizations become more mature and accelerate along the maturity curve:
- Scope of privileged users and use cases expand. You expand your sphere of protection to include more types of privileged users, sensitive systems, and privileged accounts.
- Controls become more dynamic. You add more granular controls and implement conditions and time limits to access. Ultimately, access controls become risk-based and adapt as your risk profile changes.
- Intelligence and automation increase. PAM replaced time-consuming, inconsistent manual tasks until ultimately, your system is continuously learning and adapting.
- Integrations embed PAM in your workflows. More enterprise technologies are integrated, to the point where virtually all privileged users access PAM via another system (their ITSM or IGA tools, web browser, native client, Slack, etc. etc.) making PAM virtually “invisible.”
This step-by-step method of PAM adoption helps you build a strong foundation that supports you as you scale.
Build a PAM maturity plan that’s right for you
Check out the PAM Maturity whitepaper and select the starting point that reflects your current level of PAM maturity.
The controls associated with each phase of maturity reflect the order Delinea recommends for organizations to roll out their PAM strategy. We’ll meet you where you are and help you accelerate toward your goals.
Does this sound like you?
- Secure privileged accounts in a limited way, if at all.
- Set up privileges manually, and keep track of them via spreadsheets.
- Have minimal complexity requirements for password creation and only single-factor authentication.
- Provide excess privileges to people who don’t need them.
- Share privileges among multiple administrators.
- Neglect to remove privileges when users leave the organization or change roles.
- Don’t know the breadth of web applications in use.
- Reuse accounts for multiple services.
If so, you’re in the danger zone!
Inside the PAM Maturity whitepaper, you’ll find recommendations to help you mitigate your risk right away.
Or, does this sound like you?
- Have numerous, disconnected password management and access tools and practices.
- Don’t differentiate access based on roles.
- Don’t have sufficient visibility over account usage.
- Can’t easily or automatically produce reports or compliance documentation.
- Must make periodic pushes to discover and rediscover new accounts across your network.
If so, you’re ready for enterprise PAM.
Inside the PAM Maturity whitepaper, you’ll find recommendations to help you expand your PAM program to cover more types of privileged accounts and risks.
See what it takes to succeed in an increasingly dangerous world. Get your copy of the PAM Maturity Model so you can systematically lower risk, increase business agility, and improve operational efficiency.

FREE CHECKLIST
Need a step-by-step guide for planning your strategic journey to privileged access security?



