Enterprise endpoint security demands a defense-in-depth strategy

Steve Goldberg
Endpoints, the devices people use to access company resources, are a weak spot in corporate security. Compromised endpoints are primary access points that cybercriminals use to infiltrate a network.
Two-thirds of companies are compromised by exploits that originate with an endpoint. The volume of endpoint attacks is rising, as is the sophistication of attacks. There’s a marked spike in criminals using advanced persistent threat (APT) techniques, in which an attacker uses one compromised endpoint to move laterally throughout a network by taking advantage of known vulnerabilities, elevating privileges, and persistently hacking once they’ve managed to get inside.
There are many reasons cyber criminals love endpoints
Most endpoint users aren’t technically inclined, nor do they feel the urgency or personal responsibility to prioritize endpoint security. The sheer variety of endpoints, including desktop computers, laptops, and mobile devices, all with different operating systems, versions, and browsers, adds complexity to security management and oversight.
Endpoints are typically compromised by either malware or non-malware attacks.
- Malware includes viruses and other rogue programs installed on an endpoint, which may cripple the endpoint or grant an unauthorized user access to it.
- Non-malware attacks exploit vulnerabilities in programs or applications that may already be installed on an endpoint, such as a word processing program or web browser.
The goal of an endpoint attack is often the same: wreak havoc by taking control or crippling a device, and then progressing from an individual endpoint to other network resources.
Yet “traditional” enterprise endpoint security, consisting of anti-virus installed locally on an endpoint, locking down or restricting access to potential soft spots, and applying user roles and privileges on a piece-meal, as-needed basis, has proven to be wholly inadequate. An approach like that is difficult to maintain, monitor and scale. It may also be rife with easy-to-exploit holes. That is why a comprehensive approach to endpoint security matters.
Imagine a world where you’re confident employees can access corporate resources without fear, uncertainty, or doubt that they may compromise sensitive systems. Imagine your IT staff has ensured all endpoints attempting to access business resources are secure. Imagine your users don’t feel they need to circumvent security protocols on their endpoints to do their jobs.
It’s possible. You have just imagined the best endpoint security for the enterprise.
Read on to learn about best practices for protecting endpoints and limiting the damage a compromised endpoint can cause. In this blog, I’ll outline how your organization can manage endpoint security effectively and mitigate the risk of compromised endpoints.
What is endpoint security?
Endpoint security is the practice of protecting users’ devices from internal and external cyber threats. The goal of endpoint security controls is to protect the attack surface to minimize the risk of network infiltration and compromise.
Endpoint security is a critical line of defense used to prevent cybercriminals from gaining access to a network, exfiltrating data, causing reputational or financial harm, destroying infrastructure, or even demanding a ransom.
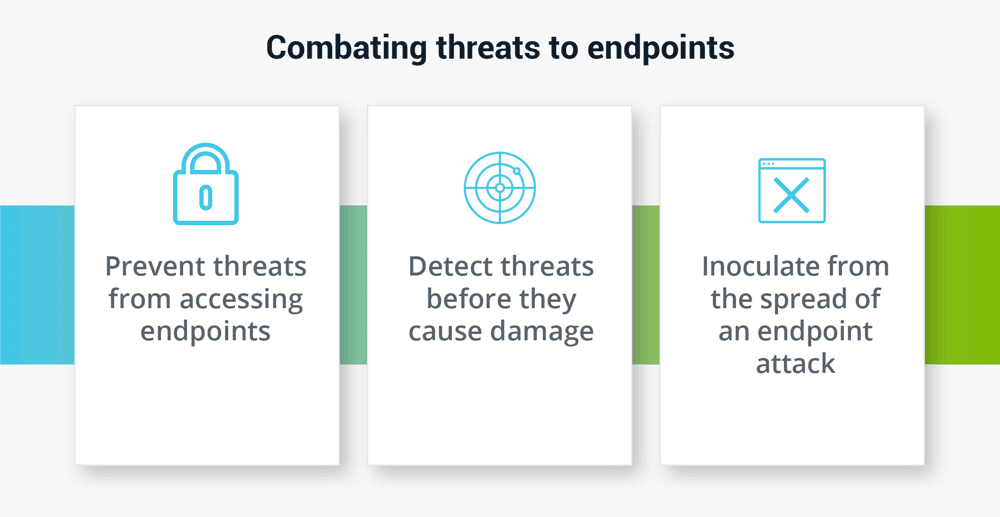
Organizations can use a number of approaches to endpoint security to combat threats at different stages of an endpoint attack:
- Prevent threats from accessing endpoints: Limit and disrupt known threats from accessing endpoints before they have the opportunity to penetrate an endpoint. Focus on quickly identifying previously unknown threats before they gain a foothold.
- Detect threats before they cause damage: Identify known threats that successfully gain access to an endpoint and continually discover new threats.
- Inoculate your organization from the spread of an endpoint attack: Limit the damage caused by infected endpoints. Contain it while you identify the root cause and apply those learnings to prevent and detect future attacks.
The proactive goal of endpoint security is to lock down entry points cybercriminals might use to access an enterprise network. In cases where locking down entry points is not feasible, minimizing damage becomes the fallback position. Implement layered endpoint security tools, combined with a structured enterprise endpoint security policy.
What are the challenges of securing endpoints?
Infrastructure teams protect the most critical information and infrastructure. But this usually involves a known quantity of systems and software, which is actively managed by knowledgeable IT professionals. Does a central system need upgrading, patching, or hardening? This is usually in their purview.
There are so many devices: desktops, laptops, tablets, phones
Endpoint security, on the other hand, is a more chaotic system with more moving parts. IT teams that manage endpoints generally have more volume and variables to address than teams that manage infrastructure security. There are So. Many. Devices. Desktops, laptops, tablets, phones. And with BYOD—bring your own device—becoming the norm and a significant percentage of users working from home, it’s even more complex.
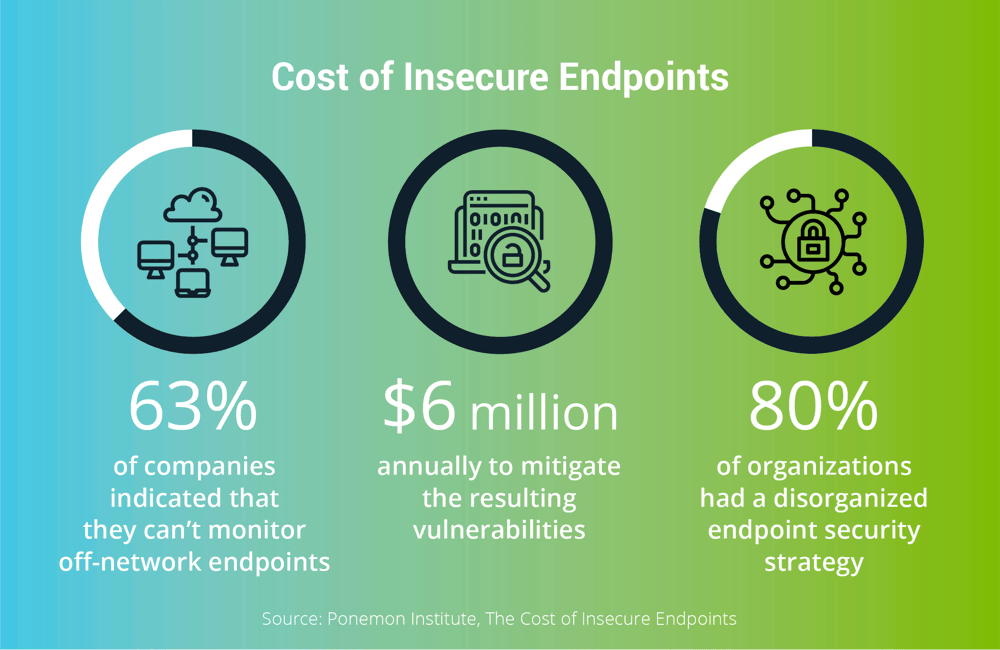
According to The Cost of Insecure Endpoints, a study conducted by the Ponemon Institute, 63% of companies indicated that they can’t monitor off-network endpoints, which results in them spending more than $6 million annually to mitigate the resulting vulnerabilities. The same survey revealed that 80% of organizations had a disorganized endpoint security strategy.
One of the biggest challenges to effective endpoint security is your users. Business users usually aren’t IT or security experts. They’re susceptible to phishing, social engineering, malware, ransomware, and various data extraction techniques. They often need to be protected from themselves—prevented from downloading a malicious app, clicking on a suspicious link, installing a suspect program, giving out personally identifiable information, or inadvertently revealing credentials.
Consider all the activities users engage in through their endpoints. They may change the time due to travel or daylight savings. They install drivers for new devices. They may change configurations and install and execute programs on the endpoints themselves. Additionally, they access many types of applications, including SaaS and browser-based web applications.
Endpoint security is not the primary concern for business users—they just want to do their jobs
Business users simply want to do their jobs and endpoint security isn’t their primary concern. They’re more focused on completing a presentation, answering an email, or performing market research for a new product. Many also use the same endpoint they use for work to perform non-work activities: check out a meme, play a game, buy something online, download an app.
When a user is working remotely, you have even less control over their devices and actions. Are they using public Wi-Fi, a secure VPN, a home network? This lack of control and huge variability makes implementing and enforcing security policies more complicated, especially if end users are given flexibility in the devices they use, the controls they have, and the places they visit on the internet.
The wide range of user activities, coupled with less security awareness, results in a higher incidence of endpoint security threats and endpoint-based attacks, including malware and ransomware.
Want to know how to secure your most vulnerable endpoints with least privilege?
Read our free eBook: Definitive Guide™ to Endpoint Privilege Management
Ransomware on the rise
Why does endpoint security matter? The casual observer may be aware of anecdotes, but not the trends: ransomware, data theft, and unauthorized access are all on the rise. They have moved from fringe, freak events to everyday occurrences with the potential to disrupt and destroy any organization. Lone, rogue cybercriminals have been replaced by organized state actors; countries are silently and systematically perpetrating attacks to gain geopolitical leverage. The stakes could not be higher.
Between 2018 and 2019, there was a 365% increase in the number of ransomware attacks, with 53% of those attacks occurring in the United States. These types of attacks are prevalent enough that all organizations—small local businesses, Fortune 500 companies, state and local governments—must be prepared to address them.
Cities may seem to be among the most common targets of ransomware attacks since they’re required to publicly disclose when they have been victimized. Yet they represent only about 10% of estimated cases; public utilities, healthcare organizations, publishing houses, and financial institutions are also frequent attack targets.
One question many businesses and public sector groups will inevitably face is: should we pay the ransom? Nearly every organization insists they will never give in to ransomware demands. Yet quietly, many are being urged to prepare for such an attack. There’s a growing demand for cybersecurity insurance, and some companies are stockpiling Bitcoin, the currency of choice for ransom payments. By some estimates, two out of three victims will eventually pay hoping for the safe (and unpublicized) return of their files or to regain access to key systems.
Good news: It’s possible to protect endpoints with a defense-in-depth strategy
The best approach to endpoint security is to implement defense-in-depth. Defense-in-depth is the strategy of layering different security controls to create a robust and redundant system. When there are multiple layers of defense for endpoints, each layer offers a different type of security, which will protect the endpoint even if one or more of the controls fails. This approach minimizes the risk of a single point of failure and is often used to address a variety of possible vulnerabilities across the range of physical, technical, and administrative layers.
Many organizations start and end their endpoint security program by installing antivirus software on every endpoint. That is an important step, but it should never be the only endpoint security solution you employ. One study of IT professionals found that only 27% believed antivirus alone would provide sufficient protection against known and unknown threats.
Where to start your endpoint security strategy
There are many different layers to an endpoint security strategy that could be put in place, yet there is only one that offers broad protection to prevent endpoint attacks from happening and limits the damage if an endpoint is breached.
Limit local administrator rights with the least privilege policy.
This is one of the most important endpoint security steps you can take since it’s proactive, and when implemented thoughtfully and maintained over time, will protect and limit access to your most important assets. With a least privilege policy in place, even if an individual endpoint is compromised, cybercriminals won’t be able to capture and leverage administrative credentials to reach critical resources.
Implementing a least privilege model ensures that each user and each endpoint have only the minimum level of access needed to do their job. It’s an important part of establishing a zero-trust environment, in which a malicious cyber criminal’s movement within a network can be contained since they won’t have access to other critical systems simply because they’ve managed to compromise one.
So users can continue doing their jobs with little to no disruption, you should also implement privilege elevation through policy-based management with allowing listing, restricting, and denying. That way you can remove local admin rights without impacting productivity.
As an example, by implementing a least privilege strategy, coupled with the ability to manage local admin rights and elevate applications, Delinea customer—the State of Indiana—ensured developers would be able to do their jobs without compromising overall network security, sacrificing endpoint security, or adding extra approval steps from IT.
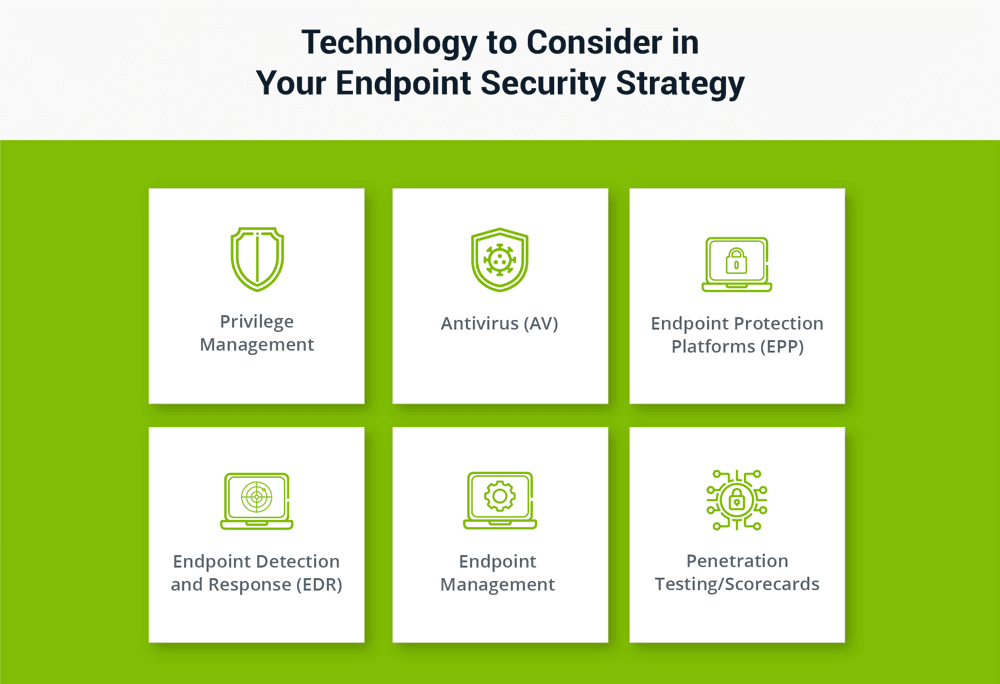
A comprehensive strategy for endpoint security should include at least three of the following techniques and technologies, and will provide you with defense-in-depth endpoint security:
-
- Privilege Management: Privilege management solutions cover endpoint privilege discovery, least privilege implementation, and ongoing, policy-based application control. Privilege management tools give you granular control over what users can do via their endpoints, including installing programs and changing configurations, as well as accessing and interacting with web applications. You can set granular policies that provide fine-grained control, for example, allowing a user access to only some functionality in a program or only certain sections of a web page.
- Antivirus (AV): Antivirus solutions are typically installed directly on an endpoint, continually scanning the system for a known virus or malware signatures. The best AV solutions continually update their list of known viruses, and quarantine suspect files and apps while preventing users from accessing malicious sites. AV solutions don’t tend to be predictive, so they are only as good as their list of known threats. Traditional AV solutions provide inadequate protection against emerging threats and trigger a high number of false positives and security alerts. 4 out of 5 successful breaches are due to zero day exploits, and on average, antivirus products miss 60% of attacks.
- Endpoint Protection Platforms (EPP): Some antivirus solutions have evolved into endpoint protection platforms. Similar to AV, they’re designed to prevent malware attacks and other malicious activity.
- Endpoint Detection and Response (EDR): By continuously collecting and analyzing data from all endpoints managed by an organization, EDR systems are an analytical surveillance endpoint protection tool. The data they collect can be used to conduct forensic analysis after a breach has occurred, and the more sophisticated ones include predictive analytics, hunting for patterns, and possible new exploits in the data. They have the added benefit of being able to assist with remediation and attack forensics in nearly real-time, providing endpoint security on demand.
- Endpoint Management: This class of software assists with endpoint inventory, keeping track of devices while also ensuring that software is patched and up to date. A good endpoint management system can help keep approved devices secure and can update them in a timely fashion to minimize damage from a zero-day exploit. These systems are prescriptive: they can protect against known vulnerabilities assuming they’re functioning properly, but they’re of little use when it comes to unknown vulnerabilities.
- Penetration Testing/Scorecards: Often conducted by an outside vendor, the idea of penetration testing is to expose your organization’s vulnerabilities, so you have time to address them before a malicious actor tries to exploit them. This is a stealthy way to identify and rectify the strengths and weaknesses of your network.
- Privilege Management: Privilege management solutions cover endpoint privilege discovery, least privilege implementation, and ongoing, policy-based application control. Privilege management tools give you granular control over what users can do via their endpoints, including installing programs and changing configurations, as well as accessing and interacting with web applications. You can set granular policies that provide fine-grained control, for example, allowing a user access to only some functionality in a program or only certain sections of a web page.
The bottom line is you must begin your endpoint security strategy with fundamental hygiene. Proactive endpoint protection based on a least privilege policy means less time and resources spent detecting an infection, chasing down cybercriminals once they’ve already entered your network, and remediating the damage.
Enterprise endpoint security is only as strong as it is usable
People don’t usually object to the need for additional security. They object to an extra burden.
Most organizations recognize the risks of lax security, so why don’t they do something about it? One of the major trade-offs in endpoint security is making it seamless and simple for a user to access needed resources. This means little to no learning curve for users, relative ease of implementation from an IT point of view, and a minimum of additional overhead to monitor that it’s being used effectively.
In other words, any enterprise-level endpoint security system you choose must balance being comprehensive with being usable. As you implement a defense-in-depth strategy, focus first on the most important and high-value endpoint security tools that have the least impact on your users. Implement and continually enforce least privilege access, restrict or remove local admin rights, then layer in antivirus solutions, EDR, or EPP solutions.
Learn more about Delinea’s privilege management solutions for endpoint security
Delinea's least privilege and application controls are an extremely effective line of defense and fill the gaps left by other enterprise endpoint security products. If an endpoint is compromised, that should be the end of the incident, rather than a foothold into a larger breach.
Privilege Manager is an all-in-one least privilege and application control solution. You can identify and remove local admin rights as well as set allow, restrict, and block policies for effective application controls.

FREE TOOL
Cybersecurity Incident Response Template