How easy is it to guess your password? (Hint: You don't want to read this!)

Ben Rice
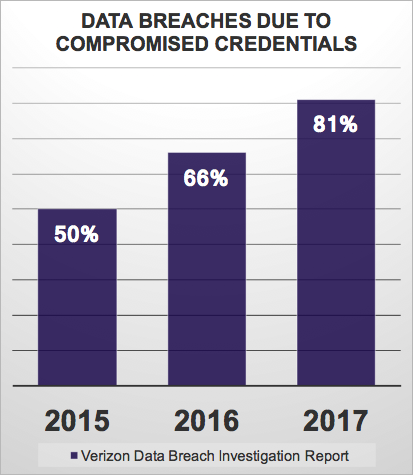
The number of account credentials that have been stolen in the last 10 years has exploded to a degree that it's unprecedented. It is now a fait accompli that many of the security tools out there can't help you as 81% of data breaches come from compromised credentials.
Let's delve into how easy it is to break into almost any account
Cybercriminals have invented the digital equivalent of a master key.
If you look at Sites like SecLists, Weakpass, and Hashes.org -- not to mention berzerk0's probable wordlists on Github which is a clever amalgam of password wordlists. Here you will find huge lists of passwords (more than 80GB worth of human-generated passwords).
What makes probable wordlists so interesting is that it is sorting of this massive compendium of passwords that have fallen into public hands following the hundreds of breaches that have occurred. This large list was then reordered from alphabetical to instead start with the most common passwords then work down the list, i.e. start with a password, 123456, etc.
This makes any automated dictionary attack extremely efficient requiring neither great computing resources nor networking capability as the most common passwords will come up for many accounts very quickly and the entire list will not even be needed.......
What are we waiting for people? Revolt against the password! Let's not stand for this anymore! Can you imagine if everyone in your neighborhood didn't change their locks when they moved in and the previous owners and others kept coming into the house at will and stealing things?
Still want to stick with your sticky notes and crummy passwords?
ArsTechnica asked three security experts to try and crack a list of over 16,000 passwords.
The most successful:
"Jeremi Gosney, a password expert with Stricture Consulting Group. Using a commodity computer with a single AMD Radeon 7970 graphics card, took only 20 hours to crack 14,734 of the hashes, a 90-percent success rate. Jens Steube, the lead developer behind oclHashcat-plus, achieved impressive results as well. (oclHashcat-plus is the freely available password-cracking software both Anderson and all crackers in this article used).So, there is not much of a barrier to entry here
Anyone can have these master keys and use them with little consequence. What are you waiting for?
Whether you are at work or thinking about your SaaS application vendors, considering home systems, registering with your school, your store-insist on multi-factor authentication (MFA), and tell your vendors to give you a password alternative. Let's not let yet another account be foisted on us where we make the user come up with the password.
Just stop using passwords. Just do it!
Learn more about passwords and application risks at Delinea's resource page, or read up on enterprise-level password management.

Pinpoint risky stored passwords in minutes



