PRIVILEGE MANAGER FEATURE
Application Control
Proactively manage and monitor all the applications running on your endpoints with policy-driven controls
- Dynamic allow/restrict/deny and elevation policies
- Real-time application analysis
- Admin approval workflows
Flexible Policy Deployment Configuration
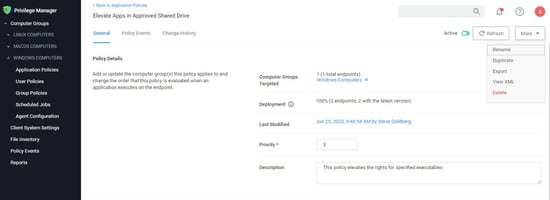
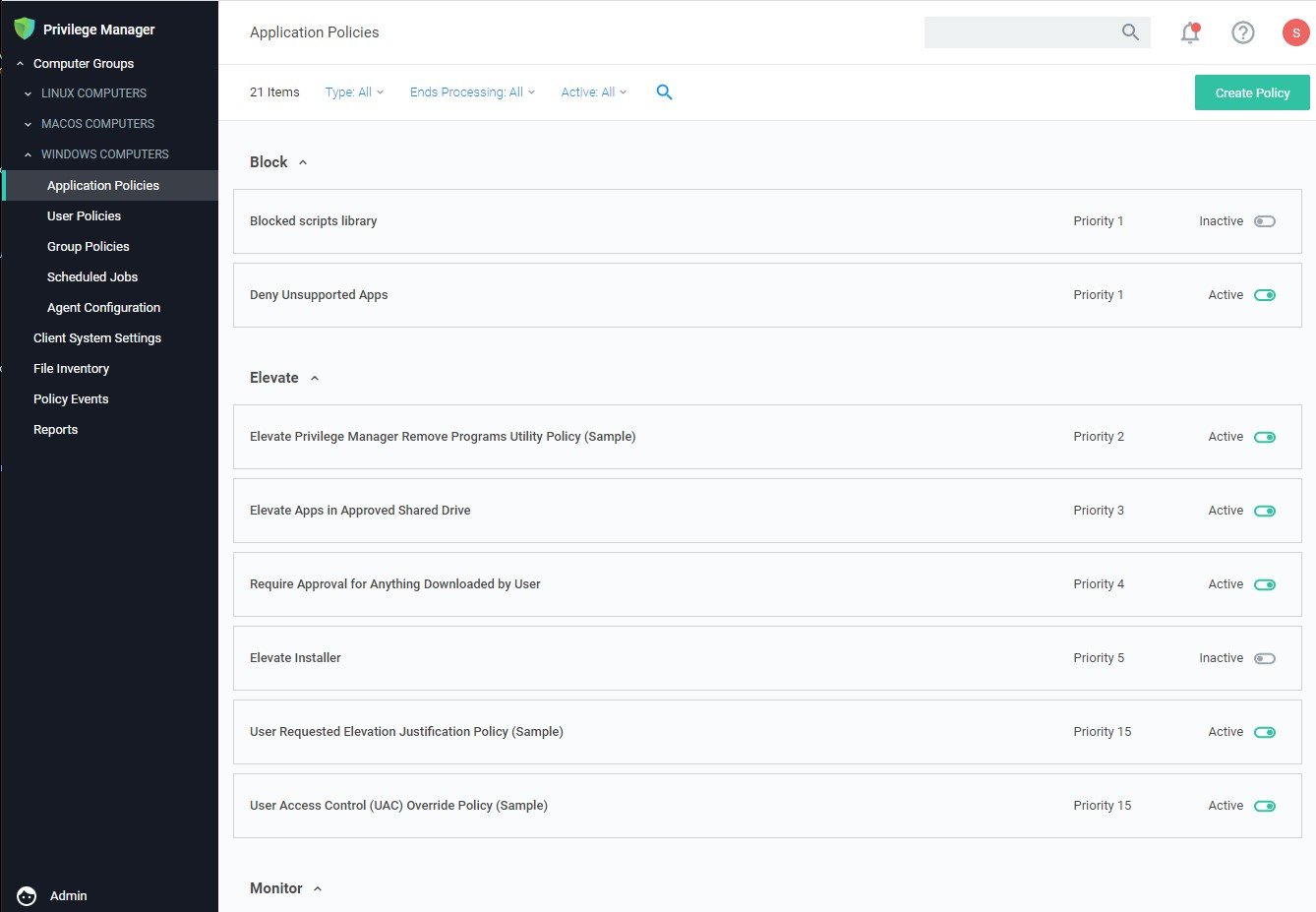
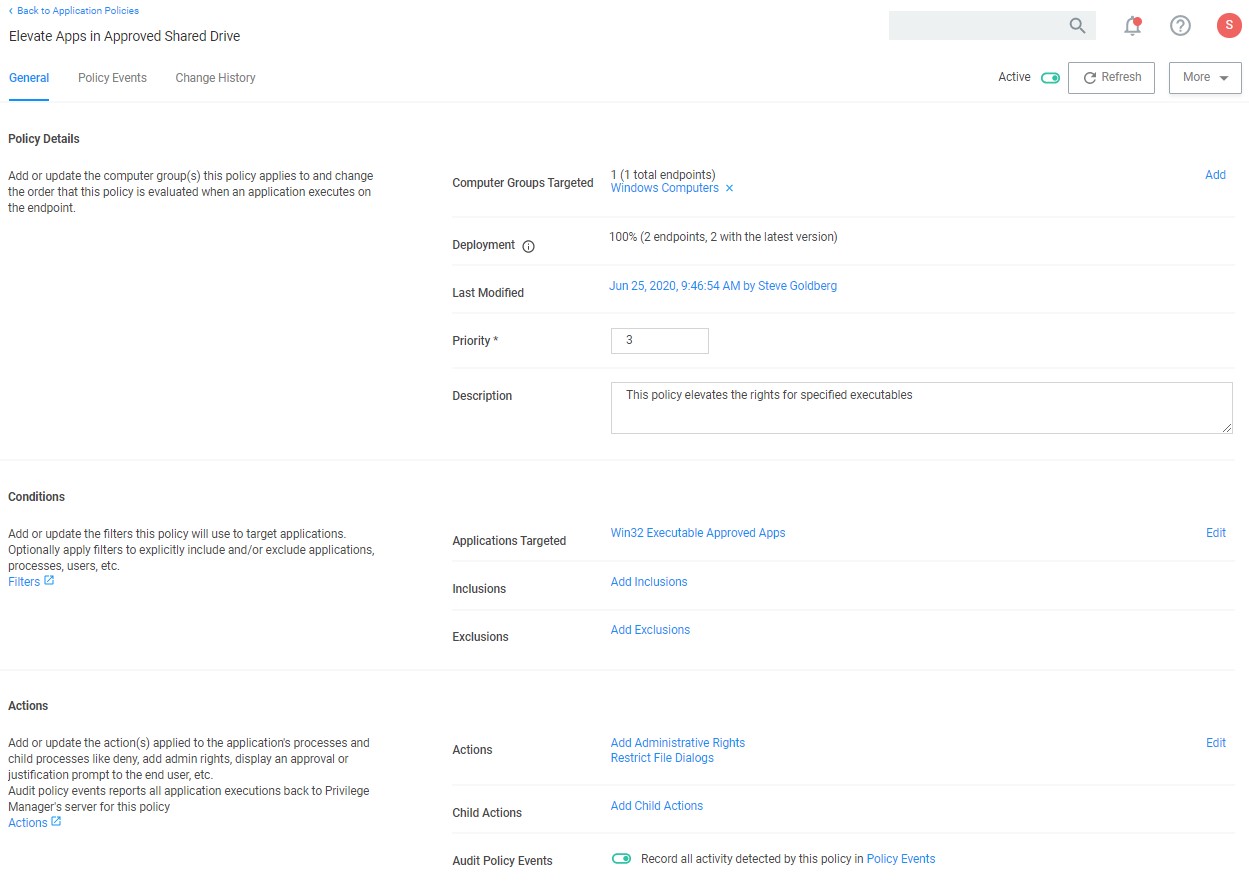
Enforce least privilege through policies for application control. You’ll start with access to a broad library of out-of-the-box policies, all of which are completely customizable. Layered policies create the parameters that dictate precisely how privileges are accessed across your network. They define what actions people can run, and where. When policy conditions are met, Privilege Manager automatically applies an action (e.g. denying, allowing, application elevation, etc.) on one or multiple assets.
Start a Free 30-Day Trial of Privilege Manager
Tailored Allow, Deny, Elevation, and Restrict Policies
Privilege Manager supports allow policies to ensure that known, trusted applications are fully supported, deny policies to deny known malicious applications based on attributes, file hash, location, or certificates, and restrict policies to prevent unknown applications from running. Restricting provides a system for discovering the unknowns and adding an action that hinges on a reputation check. Distinct from allowlist, which allows applications to run with default user-level privileges, an elevation policy applies admin credentials to specified applications. This type of policy is often paired with allowing so that employees can perform trusted tasks that require administrator credentials to complete, like installing a trusted application (Adobe) or device (printer), without involving IT support.
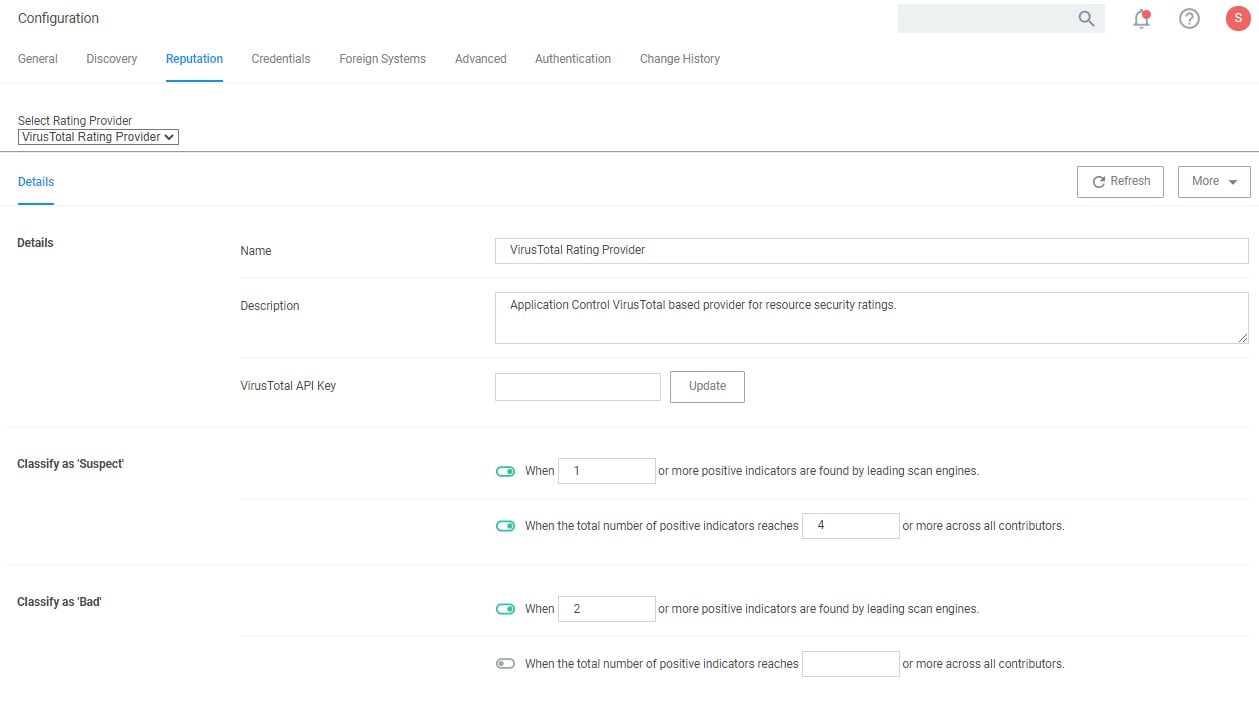
Real-time Application Analysis | Reputation Check
Privilege Manager software integrates with reputation checking software like VirusTotal to provide application analysis in real time. This unique feature allows for reputation analysis of any unknown applications in order to mitigate risk of endpoint attacks from ransomware, zero-day attacks, drive-by downloads, and other unknown malicious software. With Privilege Manager, all applications that meet a general condition (i.e. executed from a specific directory or directories, file names, types, or any applications that are disassociated with existing policies) can be sent to VirusTotal for a reputation check and analysis.
Sandboxing
Sandboxing quarantines applications so they are not allowed to execute, or only allowed to execute in a limited way so they don’t touch any system folders or underlying OS configurations. Privilege Manager supports sandboxing for applications that are not known, to ensure they do not negatively impact productivity or introduce threats to the endpoint or network.
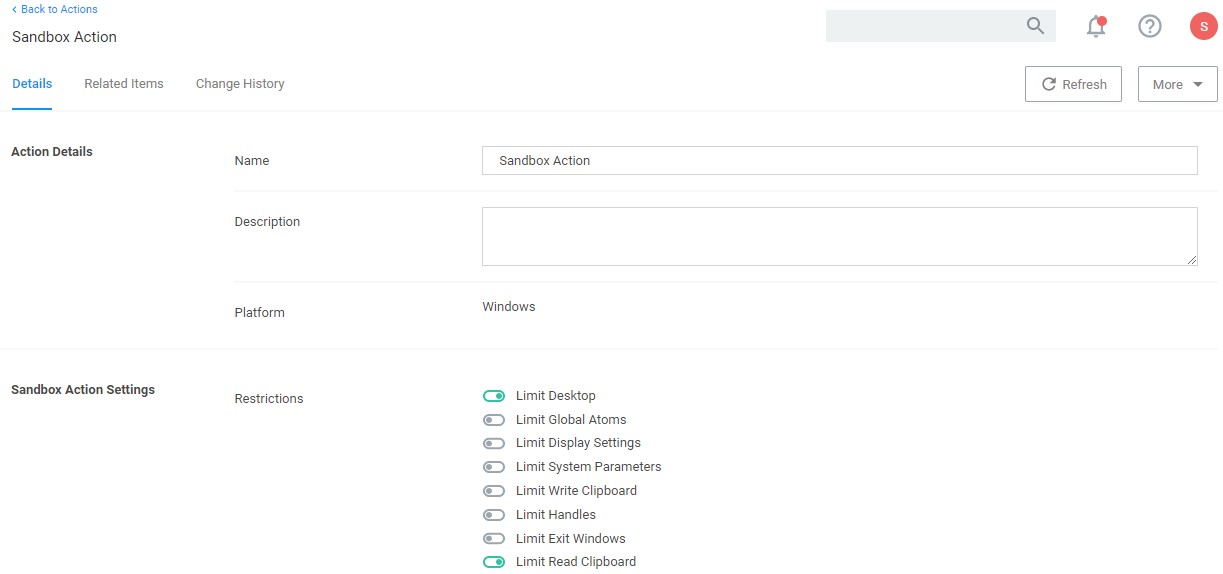
User Account Control (UAC) Override
By only elevating application privileges based upon specific policies and criteria, Privilege Manager ensures people don’t use Microsoft’s UAC capabilities to grant a dangerous or unknown application administrative rights under any circumstance.
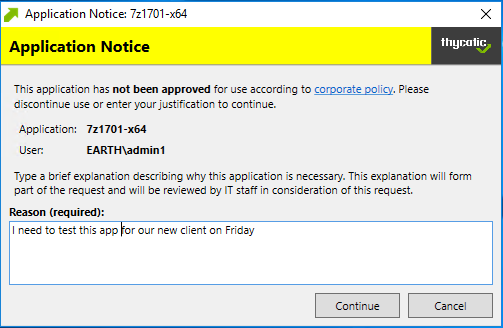
End-user Justification & Admin Approval
This policy type requires that people provide a justification for why they need to run an application before elevating with administrator privileges. User Justification refers to the policy action. Since Conditions and Actions are independent, this action can be applied to any condition.
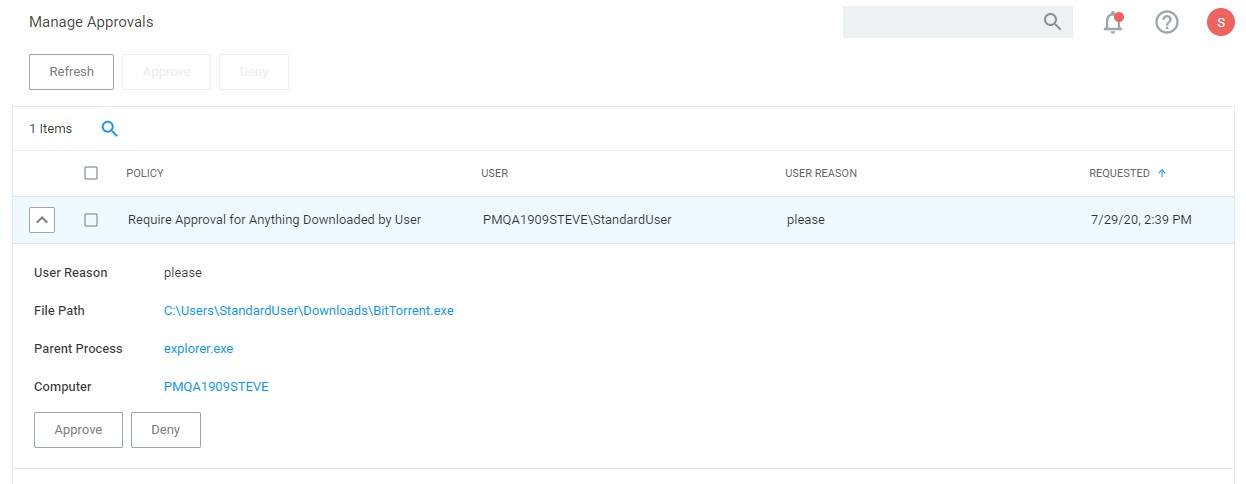
Child Process Control
Child processes are those that execute from within a file such as a PDF and are frequently how malware executes on an endpoint. Privilege Manager allows you to prohibit execution of Child Process to ensure unknown executables are restricted on your organization’s network.
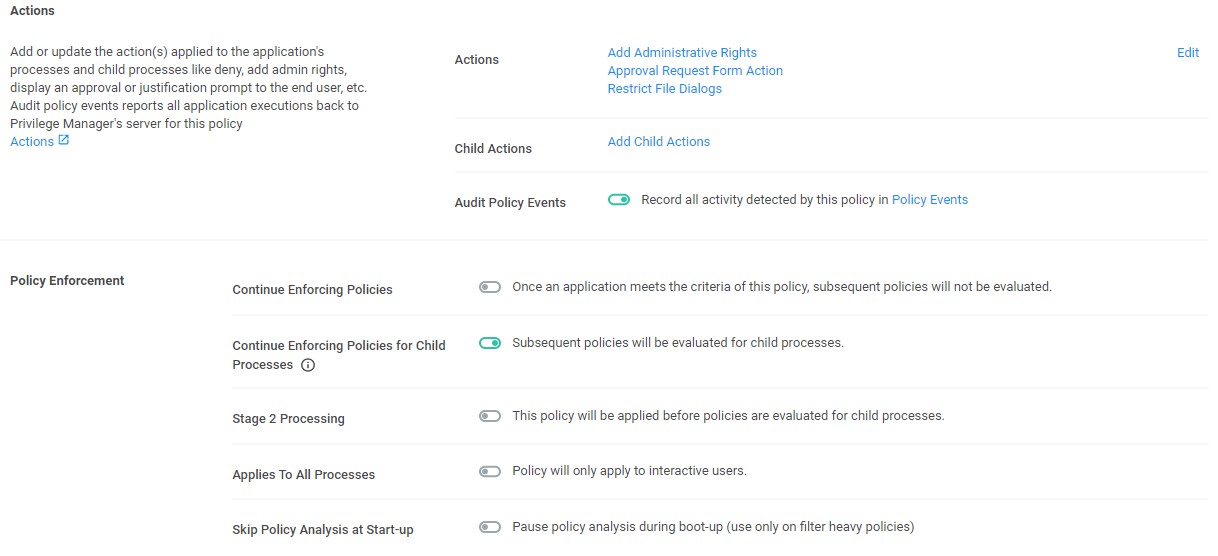
See these Privilege Manager features in action
Privilege Manager can automatically enforce your least privilege security posture through application control.